Cloud SIEM User Interface
Access Cloud SIEM
To access Cloud SIEM, in the main Sumo Logic menu select Cloud SIEM. 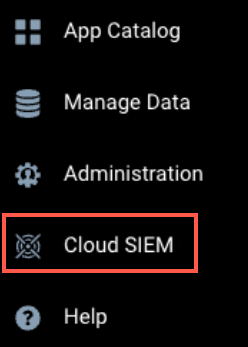
Cloud SIEM must be enabled by Sumo Logic before it is accessible to users in your organization. For more information, see Onboarding Checklist for Cloud SIEM Administrators.
Theme
You can view the user interface in a dark theme or a light theme:
- Classic UI.Click your user name in the main Sumo Logic navigation menu and select Preferences.
New UI. Click your user icon in the upper right corner of the screen and select Preferences. - Scroll down to Theme and select Dark theme or Light theme.
For more information, see Setting Account Preferences and Credentials.
Heads Up Display
The first screen you see when you access Cloud SIEM is the Heads Up Display, a single pane of information about your environment. In the center, you'll see a radar showing insights, surrounded by the signals and records used to generate the insights. On the left is summary information, and on the right is recent activity. Use this screen as the starting place for your investigations, focusing on insights as the most valuable place to start.
For more information, see Cloud SIEM Heads Up Display.
Cloud SIEM menus
New UI
The new UI provides a streamlined way to navigate in Sumo Logic. For more information, see Tour the Sumo Logic UI.
Sidebar menu
Click Cloud SIEM in the main Sumo Logic menu to open the sidebar menu. 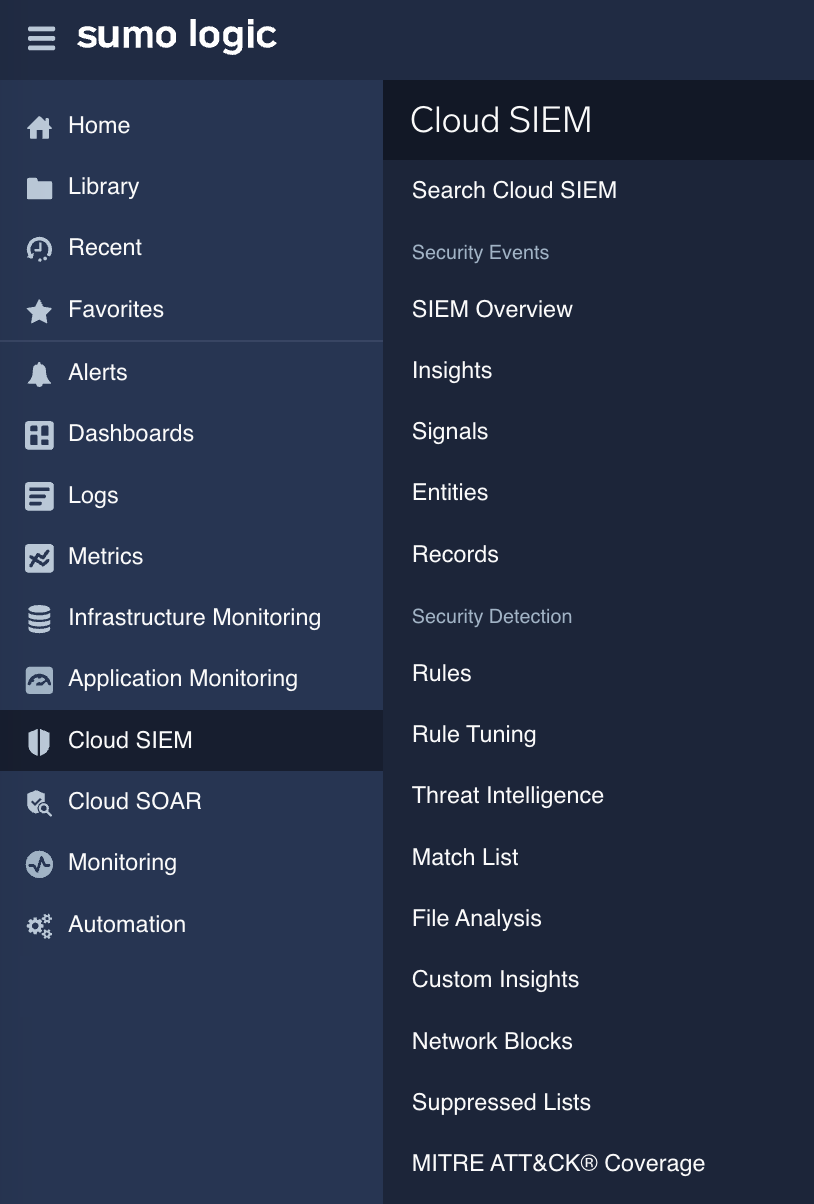
Use the Cloud SIEM sidebar menu to access:
- Search Cloud SIEM. Search for insights, signals, entities, and records. When you click in the search bar, you're prompted to select one of those types. Once you select a type, you're presented with a list of fields to filter on.
- SIEM Overview. View the Cloud SIEM Heads Up Display.
- Insights. View insights, clusters of events that require investigation. An insight is created when a high level of suspicious activity is detected for a single entity, such as a user, IP address, host, or domain.
- Signals. View signals, indicators for events of interest that fire when rule conditions are met.
- Entities. View entities, unique actors encountered in incoming messages, such as a user, IP address, or host.
- Records. View records, collections of normalized data created from a message.
- Security Detection
- Rules. Manage rules, sets of logic that create signals based on information in incoming records.
- Rule Tuning. Manage rule tuning expressions, which are extensions to rules.
- Threat Intelligence. Manage sources of threat intelligence indicators, individual data points about threats that are gathered from external sources.
- Match List. Manage match lists, lists of important indicators and identifiers that you want to be addressed by rules.
- File Analysis. Manage sources for YARA rules.
- Custom Insights. Manage custom insights, methods to generate insights on some basis other than entity Activity Scores.
- Network Blocks. Manage network blocks, groups of IP addresses that you can use in rules
- Suppressed Lists. Manage suppressed lists, lists of indicators that can suppress signal generation.
- MITRE ATT&CK Coverage. View the MITRE ATT&CK Threat Coverage Explorer, a screen that shows the MITRE ATT&CK adversary tactics, techniques, and procedures that are covered by rules in your system.
- Cloud SIEM Integrations
- Ingest Mappings. Manage the mapping for data ingestion from a data source to Cloud SIEM.
- Log Mappings. Manage log mappings, maps that tell Cloud SIEM how to build a record from the key-value pairs extracted from messages.
- Context Actions. Create actions that a Cloud SIEM analyst can use to query an external system for information about an entity, IOC, or data encountered in a record.
- Actions. Create actions to issue a notification to another service when certain events occur in Cloud SIEM.
- Enrichment. Manage elements that enrich data in Cloud SIEM.
- Automation. Create smart actions that trigger automatically when certain events occur in Cloud SIEM.
- Cloud SIEM Entities
- Groups. Manage groupings of entities that can be used in rules.
- Normalization. Manage normalizing usernames and hostnames in records during the parsing and mapping process.
- Custom Types. Manage custom types to more precisely categorize entities.
- Criticality. Adjust the severity of signals for specific entities based on some risk factor or other consideration.
- Cloud SIEM Workflow
- Insight Detection. Set the insight detection threshold.
- Insight Statuses. Manage custom insight statuses.
- Insight Resolutions. Manage custom insight resolutions.
- Tag Schemas. Manage schemas for tags, metadata you can attach to insights, signals, entities, and rules.
Top menu
This menu appears at the top of the screen: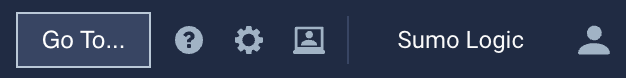
Use the top menu to access:
 Go To... Launch Sumo Logic features, including for Cloud SIEM.
Go To... Launch Sumo Logic features, including for Cloud SIEM. Help. Access links to documentation, support, community, release notes, and system status.
Help. Access links to documentation, support, community, release notes, and system status. Profile. View your notification and preference settings.
Profile. View your notification and preference settings.
Go To... menu
The Go To... menu allows you to launch Sumo Logic features, including for Cloud SIEM. To access this menu, click ![]() on the top menu.
on the top menu. 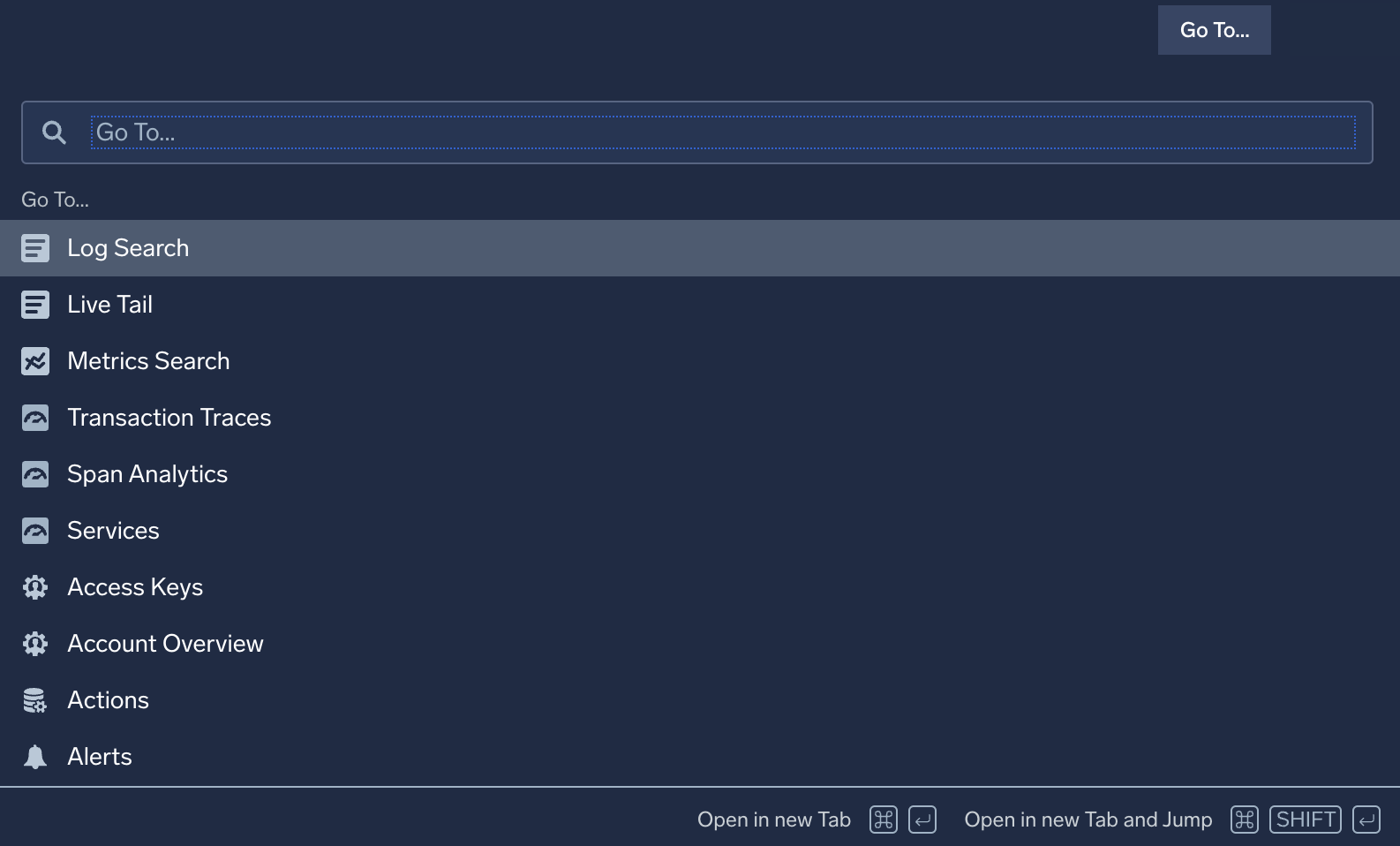
Use the Go To... menu to access these Cloud SIEM features:
- Actions. Create actions to issue a notification to another service when certain events occur in Cloud SIEM.
- Context Actions. Create actions that a Cloud SIEM analyst can use to query an external system for information about an entity, IOC, or data encountered in a record.
- Criticality. Adjust the severity of signals for specific entities based on some risk factor or other consideration.
- Custom Insights. Manage custom insights, methods to generate insights on some basis other than entity Activity Scores.
- Custom Types. Manage custom types to more precisely categorize entities.
- Enrichment. Manage elements that enrich data in Cloud SIEM.
- Entities. View entities, unique actors encountered in incoming messages, such as a user, IP address, or host.
- File Analysis. Manage sources for YARA rules.
- Ingest Mappings. Manage the mapping for data ingestion from a data source to Cloud SIEM.
- Insight Detection. Set the insight detection threshold.
- Insight Resolutions. Manage custom insight resolutions.
- Insight Statuses. Manage custom insight statuses.
- Insights. View insights, clusters of events that require investigation. An insight is created when a high level of suspicious activity is detected for a single entity, such as a user, IP address, host, or domain.
- Log Mappings. Manage log mappings, maps that tell Cloud SIEM how to build a record from the key-value pairs extracted from messages.
- Match Lists. Manage match lists, lists of important indicators and identifiers that you want to be addressed by rules.
- MITRE ATT&CK Coverage. View the MITRE ATT&CK Threat Coverage Explorer, a screen that shows the MITRE ATT&CK adversary tactics, techniques, and procedures that are covered by rules in your system.
- Network Blocks. Manage network blocks, groups of IP addresses that you can use in rules.
- Normalization. Manage normalizing usernames and hostnames in records during the parsing and mapping process.
- Records. View records, collections of normalized data created from a message.
- Rule Tuning. Manage rule tuning expressions, which are extensions to rules.
- Rules. Manage rules, sets of logic that create signals based on information in incoming records.
- Search Cloud SIEM. Search for insights, signals, entities, and records. When you click in the search bar, you're prompted to select one of those types. Once you select a type, you're presented with a list of fields to filter on.
- SIEM Overview. View the Cloud SIEM Heads Up Display.
- Signals. View signals, indicators for events of interest that fire when rule conditions are met.
- Suppressed Lists. Manage suppressed lists, lists of indicators that can suppress signal generation.
- Tag Schemas. Manage schemas for tags, metadata you can attach to insights, signals, entities, and rules.
- Threat Intelligence. Manage sources of threat intelligence indicators, individual data points about threats that are gathered from external sources.
Classic UI
The classic UI is the traditional way to navigate in Sumo Logic. For more information, see Tour the Sumo Logic Classic UI.
Top menu
This menu appears at the top of the Cloud SIEM screen: 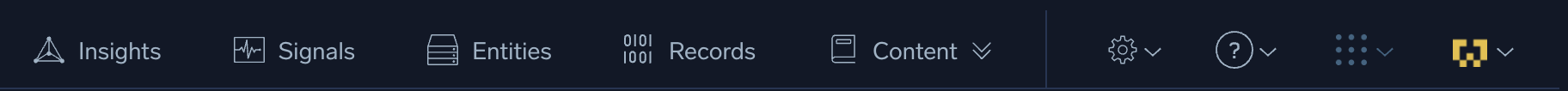
Use the top menu to access:
 Insights. View insights, clusters of events that require investigation. An insight is created when a high level of suspicious activity is detected for a single entity, such as a user, IP address, host, or domain.
Insights. View insights, clusters of events that require investigation. An insight is created when a high level of suspicious activity is detected for a single entity, such as a user, IP address, host, or domain. Signals. View signals, indicators for events of interest that fire when rule conditions are met.
Signals. View signals, indicators for events of interest that fire when rule conditions are met. Entities. View entities, unique actors encountered in incoming messages, such as a user, IP address, or host.
Entities. View entities, unique actors encountered in incoming messages, such as a user, IP address, or host. Records. View records, collections of normalized data created from a message.
Records. View records, collections of normalized data created from a message. Content. Create Cloud SIEM content, such as rules.
Content. Create Cloud SIEM content, such as rules. Configuration. Configure Cloud SIEM.
Configuration. Configure Cloud SIEM. Help. Access feature guides, documentation, release notes, and system status.
Help. Access feature guides, documentation, release notes, and system status. Switch Apps. Access the Sumo Logic Log Analytics Platform or Cloud SOAR (if enabled in your organization).
Switch Apps. Access the Sumo Logic Log Analytics Platform or Cloud SOAR (if enabled in your organization). Profile. View your Cloud SIEM username and time zone.
Profile. View your Cloud SIEM username and time zone.
Content menu
The Content menu allows you to create elements to customize Cloud SIEM. To access the menu, click Content on the top menu. 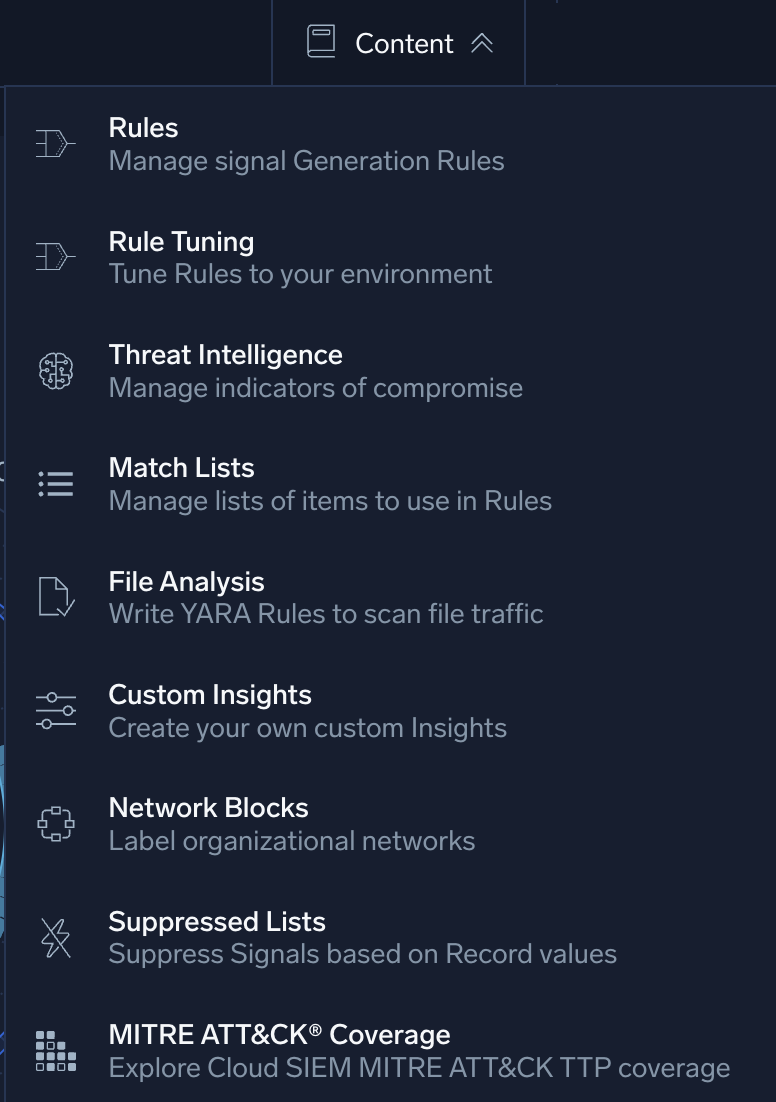
Use the Content menu to access:
- Rules. Manage rules, sets of logic that create signals based on information in incoming records.
- Rule Tuning. Manage rule tuning expressions, which are extensions to rules.
- Threat Intelligence. Manage sources of threat intelligence indicators, individual data points about threats that are gathered from external sources.
- Match Lists. Manage match lists, lists of important indicators and identifiers that you want to be addressed by rules.
- File Analysis. Manage sources for YARA rules.
- Custom Insights. Manage custom insights, methods to generate insights on some basis other than entity Activity Scores.
- Network Blocks. Manage network blocks, groups of IP addresses that you can use in rules.
- Suppressed Lists. Manage suppressed lists, lists of indicators that can suppress signal generation.
- MITRE ATT&CK Coverage. View the MITRE ATT&CK Threat Coverage Explorer, a screen that shows the MITRE ATT&CK adversary tactics, techniques, and procedures that are covered by rules in your system.
Configuration menu
The Configuration menu allows you to configure Cloud SIEM. To access this menu, click ![]() on the top menu.
on the top menu.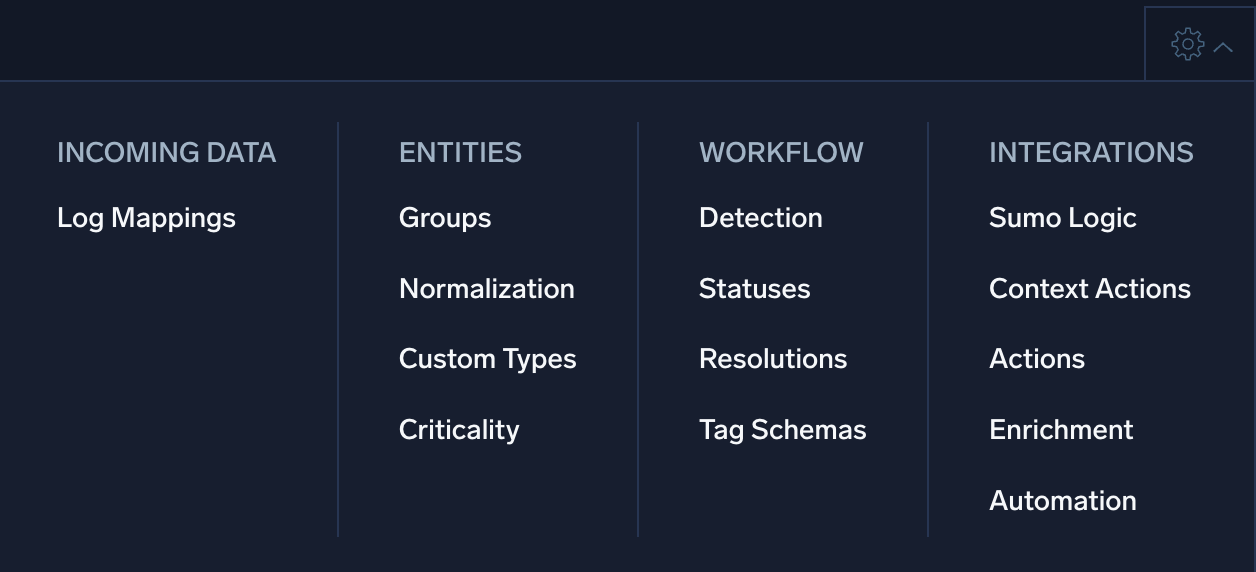
Use the Configuration menu to access:
- Incoming Data
- Log Mappings. Manage log mappings, maps that tell Cloud SIEM how to build a record from the key-value pairs extracted from messages.
- Entities
- Groups. Manage groupings of entities that can be used in rules.
- Normalization. Manage normalizing usernames and hostnames in records during the parsing and mapping process.
- Custom Types. Manage custom types to more precisely categorize entities.
- Criticality. Adjust the severity of signals for specific entities based on some risk factor or other consideration.
- Workflow
- Detection. Set the insight detection threshold.
- Statuses. Manage custom insight statuses.
- Resolutions. Manage custom insight resolutions.
- Tag Schemas. Manage schemas for tags, metadata you can attach to insights, signals, entities, and rules.
- Integrations
- Sumo Logic. Configure mapping of message fields to record attributes.
- Context Actions. Create actions that a Cloud SIEM analyst can use to query an external system for information about an entity, IOC, or data encountered in a record.
- Actions. Create actions to issue a notification to another service when certain events occur in Cloud SIEM.
- Enrichment. Manage elements that enrich data in Cloud SIEM.
- Automation. Create smart actions that trigger automatically when certain events occur in Cloud SIEM.