Rules Status
This article describes the status of Cloud SIEM rules and how to address rules that are in a degraded or failed state.
View a rule's status
You can see a rule's status while viewing the rule:
- On the rules list page:
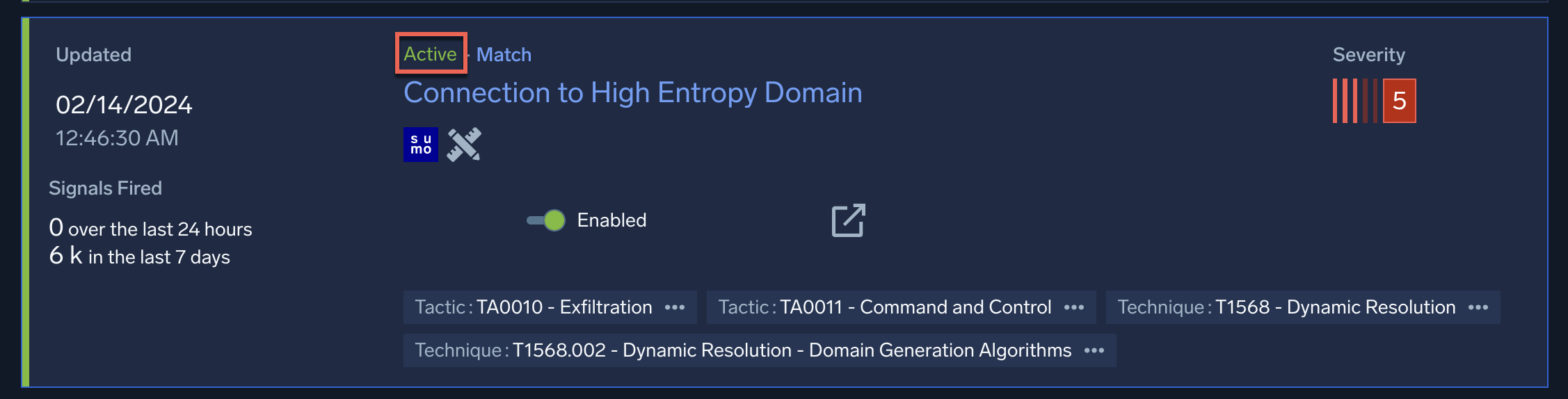
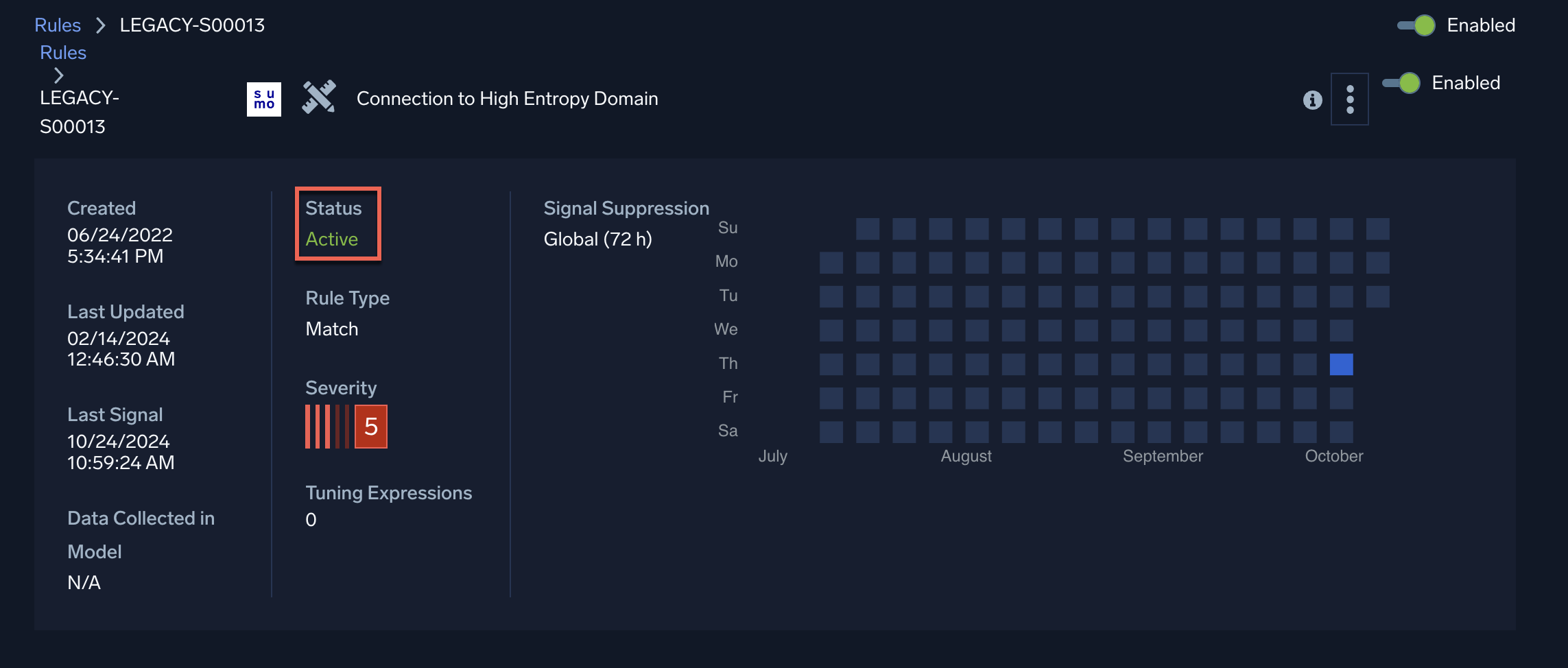
- On the rule details page:
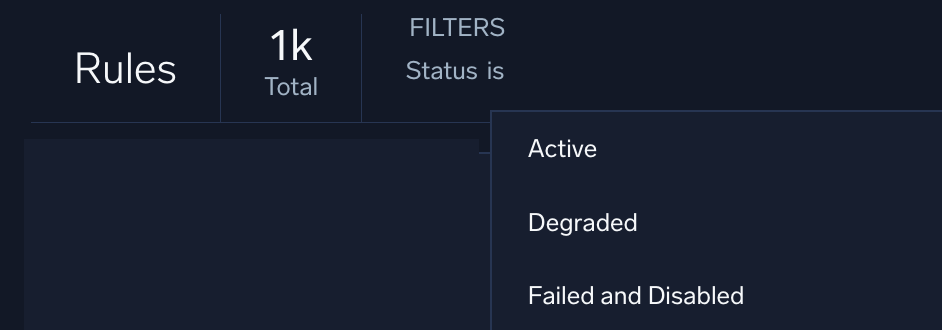
Search for rules by status
- New UI. In the main Sumo Logic menu select Cloud SIEM > Rules. You can also click the Go To... menu at the top of the screen and select Rules.
- Click Filters at the top of the Rules screen.
Classic UI. In the top menu select Content > Rules. - Select the Status field.
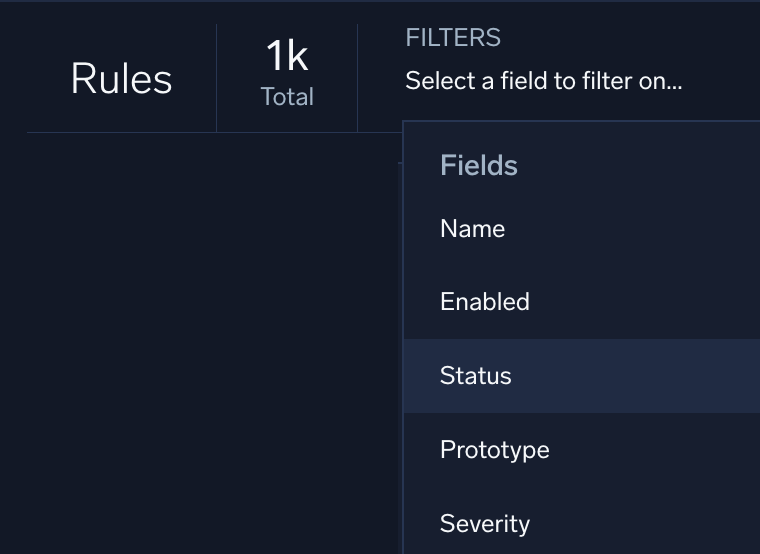
- For Operator select is.
- Select a status.
Kinds of rule status
Following are the different kinds of rule status. A rule's status can change depending on whether it exceeds rule limits.
| Status | Description | Action required |
|---|---|---|
| Active | The rule is executing normally. | No action required. |
| Degraded | The rule encountered a problem during processing and is removed from execution until the problem is resolved. | Click the information button |
| Disabled | The rule was manually disabled using the toggle in the UI, or was disabled with the API. | Enable the rule with the toggle in the UI, or enable the rule with the API. |
| Failed | The rule encountered a problem that resulted in its being automatically disabled. For example, processing the rule caused the system to exceed a rule limit. | Click the information button After addressing the reason for the failure, enable the rule with the toggle in the UI, or enable the rule with the API. |
| Pending Baseline | The baseline for the first seen rule or outlier rule is being generated. | Click the information button |
Degraded rules
A degraded rule is one that has been temporarily removed from execution because a problem was encountered during rule processing. After the problem is resolved, the rule returns to execution.
Rules can be degraded for many reasons, such as a failure to parse the rule. If the rule is degraded because it is approaching a rule limit, it is removed for one hour to allow processing to catch up, and at the end of the hour, the rule is allowed to execute again and its status changes back to Active.
If you write a custom rule that becomes degraded, you must tune the rule to correct the problem. Create a rule tuning expression to address the portion of the rule causing the rule degradation.
Following are some situations when a rule can be become degraded:
- When a rule cannot be parsed, a message like this can appear when you click the information button on the "Degraded" rule status:
Failure to parse rule: Line 1:2 mismatched input 'Unknown' expecting {<EOF>, '[', '.', AND, BETWEEN, IN, IS, LIKE, MATCHES, NOT, OR, RLIKE, EQ, '<=>', '<>', '!=', '<', LTE, '>', GTE, '+', '-', '*', '/', '%', WS} - Rules have a limit on the number of records per second they can evaluate. If there is a value used in the "group by" field that causes the rule to exceed that threshold, Cloud SIEM might display a message like this when you click the information button on the "Degraded" rule status:
The aggregation on the group key 'admin@company.com' has a record volume exceeding the supported limit, and has been disabled. Consider tuning the rule to exclude records producing this group key.
Troubleshoot baseline problems
Sometimes there may be a problem creating a baseline for a first seen rule or outlier rule. In these cases, the rule might enter a Degraded, Failed, or Pending Baseline state. Clicking the information button ![]() on the status label in most cases will provide enough information to resolve the problem. But if not, you can do additional troubleshooting:
on the status label in most cases will provide enough information to resolve the problem. But if not, you can do additional troubleshooting:
- Check the Sumo Logic status page to see if there’s an outage in your deployment. If the system is down, it cannot generate the baseline.
- If the rule has a Degraded status because it failed to parse, fix the rule so that it parses correctly. A baseline cannot be built if the rule does not successfully parse. One thing you can do is ensure that a matching expression for the rule parses correctly is to use the compatible core platform literals.
- If the rule has a Failed status, clicking the information button might show that the amount of data requested is too large to return (see Rule limits). In this case, create a more filtered baseline focusing on the exact activity you want to capture.
- If the rule has a persistent Pending Baseline status, there might not be enough data in the system to build the baseline:
- Check the ingest configuration of your Cloud SIEM data sources and confirm the appropriate records are being added to the system.
- The matching expression may not be using the right fields. Cloud SIEM records are normalized to a defined schema. The matching expression and all other fields should use that schema and not the raw log field names.
- There may not be enough activity to build a baseline. Expand the baseline retention period to gather more activity.
- Make sure that the Sumo Logic system has been active and ingesting data for the full baseline retention period. For example, if the rule has a default baseline retention period of 90 days, but your company only started using Sumo Logic a few days ago, then the rule will remain in the Pending Baseline state until 90 days have passed. To resolve the issue, change the baseline retention period window.
Rule limits
Limits are set on how often a rule fires so that the system is not overloaded. For example, if a rule fires too many signals in an hour, it can cause performance problems for all rule processes. If a rule exceeds a limit, its rule status changes from Active to Failed and the rule is disabled.
| Type | Limit |
|---|---|
| Signals per hour | 100K |
| Signals per 24 hours | 1M |
Query for rule status changes
You can query audit logs for rule status changes. For more information about querying audit logs, see Cloud SIEM Audit Logging and Cloud SIEM audit log definitions.
Query for disabled rules
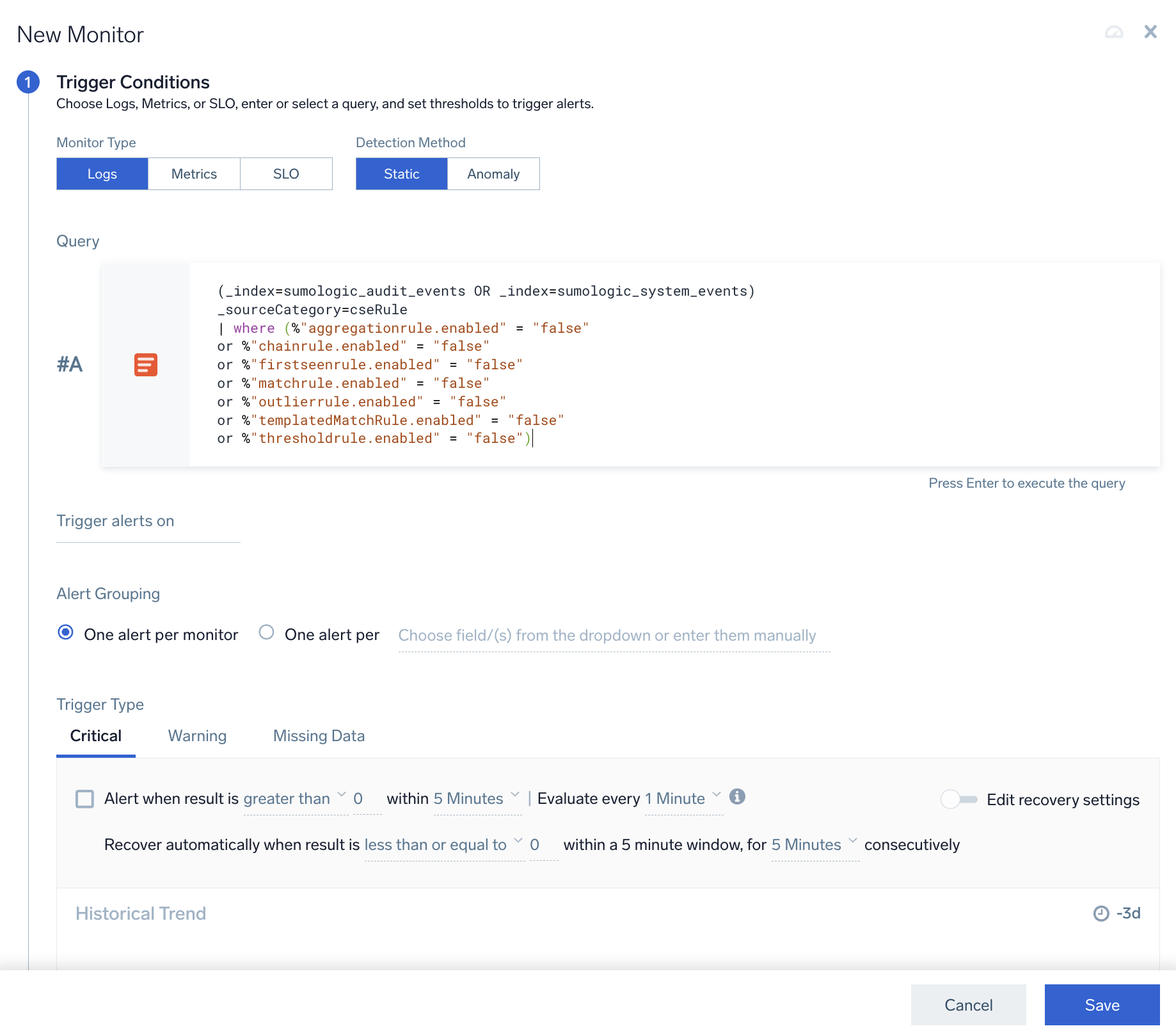
Use the following query to find rules that are disabled. It finds rules that are manually disabled by users (in _index=sumologic_audit_events) or automatically disabled by the system (in _index=sumologic_system_events).
(_index=sumologic_audit_events OR _index=sumologic_system_events) _sourceCategory=cseRule
| where (%"aggregationrule.enabled" = "false"
or %"chainrule.enabled" = "false"
or %"firstseenrule.enabled" = "false"
or %"matchrule.enabled" = "false"
or %"outlierrule.enabled" = "false"
or %"templatedMatchRule.enabled" = "false"
or %"thresholdrule.enabled" = "false")
Query for updated rules
Use the following query to find rules that have been updated. This query finds rules that are updated for any reason. The update may not result in a status change for the rule.
(_index=sumologic_audit_events OR _index=sumologic_system_events) _sourceCategory=cseRule
| where (eventName = "AggregationRuleUpdated"
or eventName = "ChainRuleUpdated"
or eventName = "FirstSeenRuleUpdated"
or eventName = "MatchRuleUpdated"
or eventName = "OutlierRuleUpdated"
or eventName = "TemplatedMatchRuleUpdated"
or eventName = "ThresholdRuleUpdated" )
| sort by eventName asc
Create a monitor to alert on rule status changes
You can create a monitor to generate alerts when rules statuses change. This will alert you when you need to take action.
For example, you could use the query for disabled rules above in your monitor. It will alert when rules are disabled.