Amazon Route53 Resolver Security

Amazon Route 53 Resolver is a highly available cloud-based DNS service from Amazon. The Sumo Logic Route 53 Resolver Security app enables you to monitor both Query Logs, and if in use, the DNS Firewall logs.
Query logging enables visibility to inbound and outbound DNS queries to the Resolver endpoint. Integrating the logs with Sumo Logic provides insights such as queries by location or instance id.
With Route 53 Resolver DNS Firewall, you can filter and regulate outbound DNS traffic for your virtual private cloud (VPC). To do this, you create reusable collections of filtering rules in DNS Firewall rule groups, associate the rule groups to your VPC. By integrating these DNS Firewall logs with Sumo Logic you can monitor VPC activity for misconfigurations and suspicious traffic.
DNS Firewall is a feature of Route 53 Resolver and doesn't require any additional Resolver setup to use.
Log types
The Amazon Route 53 Resolver Security app uses:
If you aren't using DNS Resolver Firewall, the Amazon Route 53 Resolver Security app can still provide security insights from your resolver query logs, but data specific to the DNS Resolver Firewall data will not populate in the corresponding panels.
Collect Logs for the Amazon Route 53 Resolver Security app
This topic has instructions for collecting logs for the Amazon Route 53 Resolver Security app.
Before you start
If you want to set up Route 53 Resolver DNS Firewall, see the Amazon Developer Guide for instructions.
Set up collection
- Create an AWS Kinesis Firehose for Logs Source. Make a note of the HTTP Source Address for the source. You'll need it for the Cloudformation template below.
- Set up CloudWatch to stream logs to Kinesis Data Firehose using the Cloudformation Template
- In this step, enable DNS query logging, as described in Managing Resolver query logging configurations in AWS help.
- When you select the type of AWS resource to which you want Resolver to send query logs, choose Kinesis Data Firehose delivery stream as the Destination for the Query Logs.
- Click Browse streams and select the Kinesis Data Firehose delivery stream that was created by the Sumo Logic CloudFormation template. It should start with
Kinesis-Logs-<random-string>. - Click Add VPC in the VPCs to log queries for section.
- Complete your configuration by clicking Configure query logging at the bottom of the page.
- Your new configuration will now be listed.
Sample log messages
Route 53 Resolver query log example
Installing the Amazon Route 53 Resolver Security app
To install the app, do the following:
Next-Gen App: To install or update the app, you must be an account administrator or a user with Manage Apps, Manage Monitors, Manage Fields, Manage Metric Rules, and Manage Collectors capabilities depending upon the different content types part of the app.
- Select App Catalog.
- In the 🔎 Search Apps field, run a search for your desired app, then select it.
- Click Install App.
note
Sometimes this button says Add Integration.
- Click Next in the Setup Data section.
- In the Configure section of your respective app, complete the following fields.
- Field Name. If you already have collectors and sources set up, select the configured metadata field name (eg _sourcecategory) or specify other custom metadata (eg: _collector) along with its metadata Field Value.
- Click Next. You will be redirected to the Preview & Done section.
Post-installation
Once your app is installed, it will appear in your Installed Apps folder, and dashboard panels will start to fill automatically.
Each panel slowly fills with data matching the time range query received since the panel was created. Results will not immediately be available but will be updated with full graphs and charts over time.
Viewing Amazon Route 53 Resolver Security dashboards
All dashboards have a set of filters that you can apply to the entire dashboard. Use these filters to drill down and examine the data to a granular level.
- You can change the time range for a dashboard or panel by selecting a predefined interval from a drop-down list, choosing a recently used time range, or specifying custom dates and times. Learn more.
- You can use template variables to drill down and examine the data on a granular level. For more information, see Filtering Dashboards with Template Variables.
- Most Next-Gen apps allow you to provide the scope at the installation time and are comprised of a key (
_sourceCategoryby default) and a default value for this key. Based on your input, the app dashboards will be parameterized with a dashboard variable, allowing you to change the dataset queried by all panels. This eliminates the need to create multiple copies of the same dashboard with different queries.
Query Logging Overview
The Query Logging Overview Dashboard provides insights into DNS activities such as DNS queries by location, VPC and instance ID. Additional security information is provided, including blocked and alerted DNS queries from the Route 53 DNS Resolver Firewall, and threat intel matches from Sumo Logic threat intelligence.
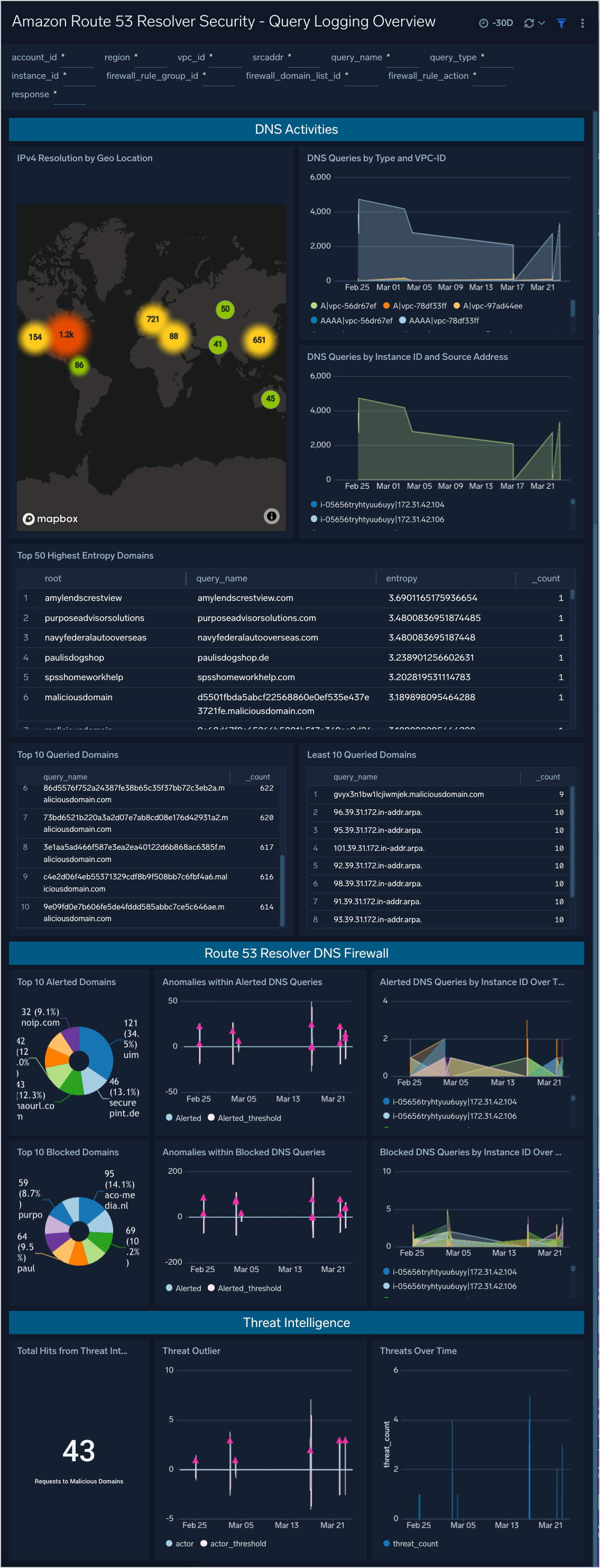
Use this dashboard to:
- Identify unusual or changes in DNS activity.
- Identify possible malicious or anomalous behavior by reviewing high entropy domains, most and least queried domains.
- Analyze DNS requests violating your Route 53 DNS Resolver Firewall policies.
- Review Threat Intel matches.
Panels include:
- IPv4 Resolution by Geo Location
- Top 10 Queried Domains
- Least 10 Queried Domains
- DNS Queries Over 24H by Type and VPC-ID
- DNS Queries by Instance ID and Source Address
- Top 50 Highest Entropy Domains
- Total Hits from Threat Intel Source
- Threats Over Time
- Threat Outlier
- Anomalies within Alerted DNS Queries
- Anomalies within Blocked DNS Queries
- Alerted DNS Queries by Instance ID Over Time
- Top 10 Alerted Domains
- Top 10 Blocked Domains
- Blocked DNS Queries by Instance ID Over Time
Resolver DNS Firewall
The Resolver DNS Firewall Dashboard provides monitoring and insights into DNS Firewall activity.
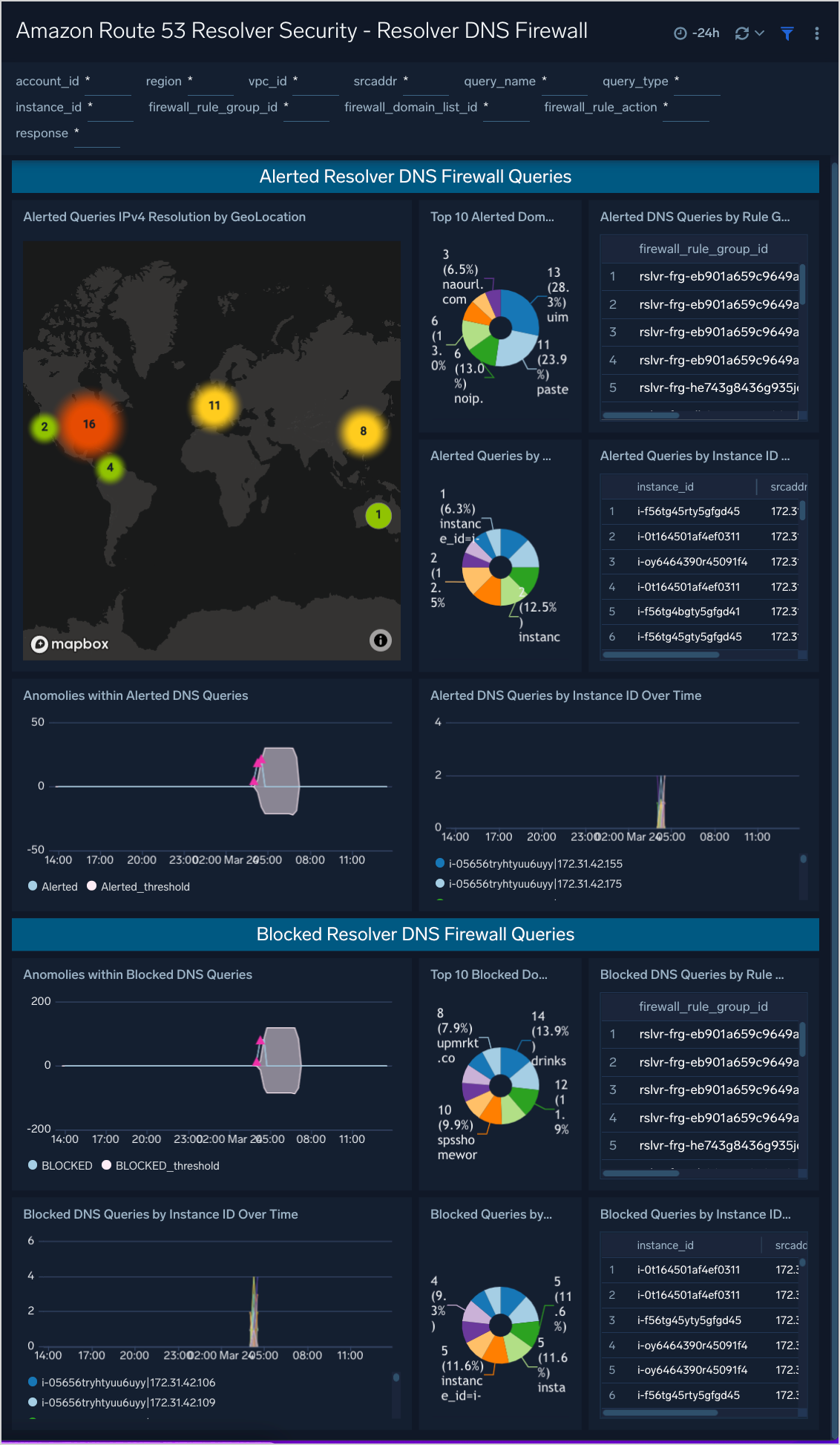
Use this Dashboard to:
- Analyze Blocked and Alerted DNS Queries by Domain, Instance ID, Rule Group ID, Domain List ID
- Help identify possible DNS exfiltration attempts
- Identify communications to known bad domains
Panels include:
- Alerted Queries IPv4 Resolution by GeoLocation
- Alerted DNS Queries by Rule Group ID & Domain List ID
- Alerted Queries by Instance ID and Source Address
- Anomalies within Alerted DNS Queries
- Alerted DNS Queries by Instance ID Over Time
- Top 10 Alerted Domains
- Blocked DNS Queries by Rule Group ID & Domain List ID
- Blocked Queries by Instance ID and Source Address
- Anomalies within Blocked DNS Queries
- Blocked DNS Queries by Instance ID Over Time
- Top 10 Blocked Domains
Security Detail
Security Detail Dashboard provides insights into DNS activities such as number of DNS requests and data throughput by VPC and instance ID. The Dashboard also provides a detailed drill down per request, displaying information such as the request, request type, ASN Number and ASN Org Name and DNS Resolver Firewall Actions.
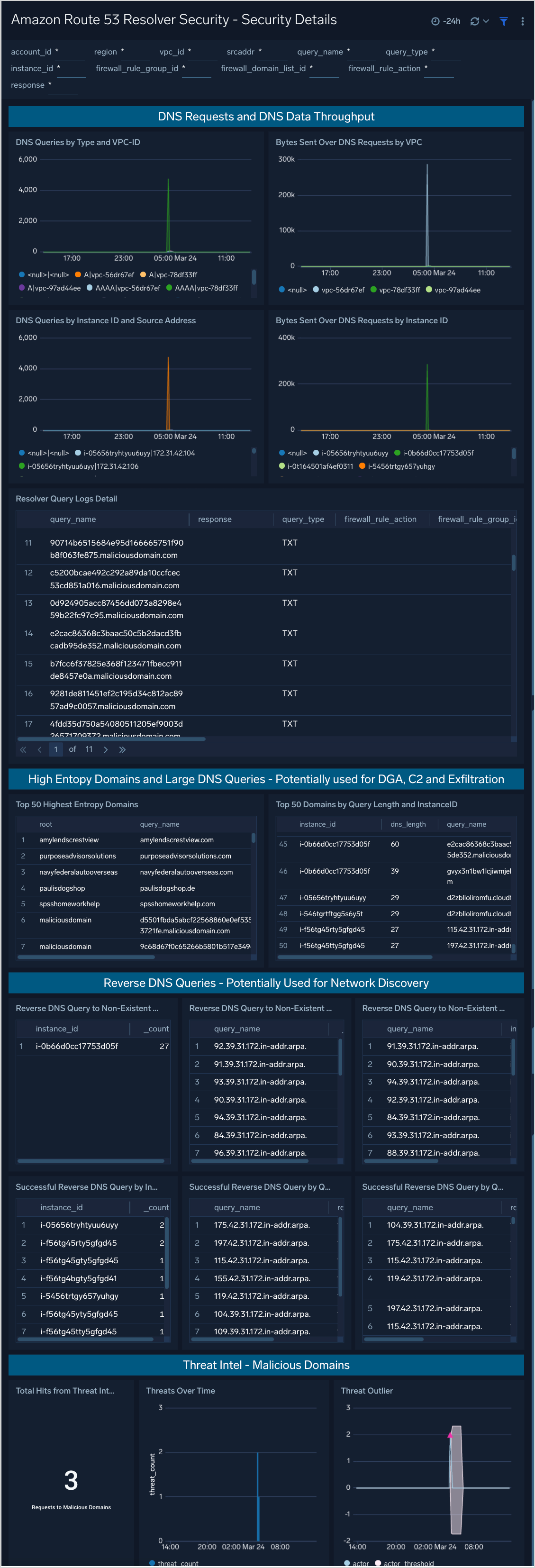
Use this Dashboard to identify:
- Possible data exfiltration over DNS
- Communication to possible DGA Domains
- Beaconing behavior
- Potential Network Footprinting/Discovery Activity
- Communication to known Malicious Domains using Threat Intelligence
Panels include:
- DNS Queries Over 24H by Type and VPC-ID
- DNS Queries by Instance ID and Source Address
- Bytes Sent Over DNS Requests by Instance ID
- Bytes Sent Over DNS Requests by VPC
- Top 50 Highest Entropy Domains
- Top 50 Domains by Query Length and InstanceID
- DNS Queries by Instance ID and Source Address
- Resolver Query Logs Detail
- Reverse DNS Query to Non-Existent Domain by Query Name & Instance ID
- Reverse DNS Query to Non-Existent Domain by Query Name
- Reverse DNS Query to Non-Existent Domain by Instance ID
- Successful Reverse DNS Query by Query Name & Instance ID
- Successful Reverse DNS Query by nstance ID
- Successful Reverse DNS Query by Query Name
- Total Hits from Threat Intel Source
- Threats Over Time
- Threat Outlier
Threat Intel
The Threat Intel Dashboard provides details of AWS DNS Resolver Queries that matches the Sumo Logic threat intelligence data with known malicious IP addresses and Domains, allowing for real-time security analytics to help detect threats in your environment and protect against cyber attacks.
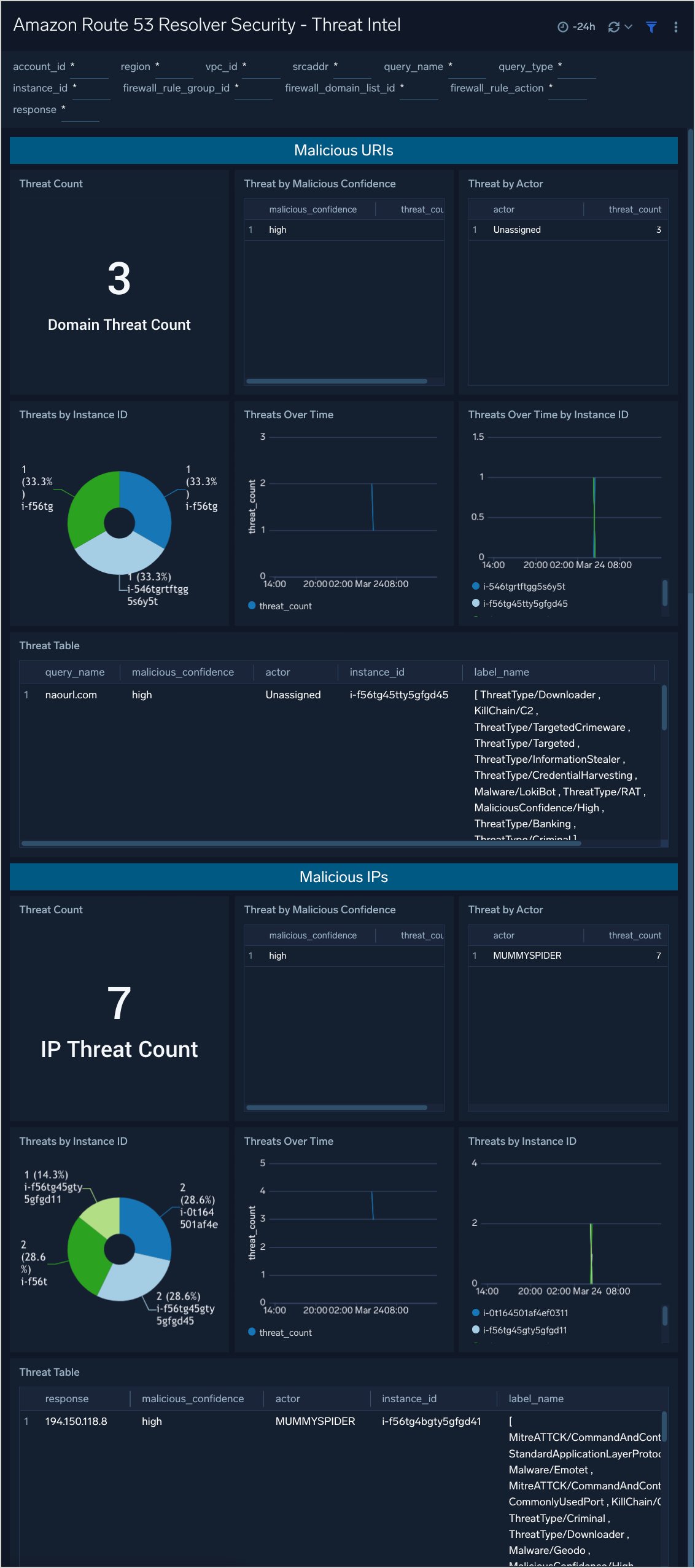
Panels include:
- Threat Count
- Threat by Malicious Confidence
- Threat by Actor
- Threats by Instance ID
- Threats Over Time
- Threats Over Time by Instance ID
- Threat Table
- Malicious URIs
- Malicious IPs
Upgrade/Downgrade the Amazon Route 53 Resolver Security app (Optional)
To update the app, do the following:
Next-Gen App: To install or update the app, you must be an account administrator or a user with Manage Apps, Manage Monitors, Manage Fields, Manage Metric Rules, and Manage Collectors capabilities depending upon the different content types part of the app.
- Select App Catalog.
- In the Search Apps field, search for and then select your app.
Optionally, you can identify apps that can be upgraded in the Upgrade available section. - To upgrade the app, select Upgrade from the Manage dropdown.
- If the upgrade does not have any configuration or property changes, you will be redirected to the Preview & Done section.
- If the upgrade has any configuration or property changes, you will be redirected to the Setup Data page.
- In the Configure section of your respective app, complete the following fields.
- Field Name. If you already have collectors and sources set up, select the configured metadata field name (eg _sourcecategory) or specify other custom metadata (eg: _collector) along with its metadata Field Value.
- Click Next. You will be redirected to the Preview & Done section.
Post-update
Your upgraded app will be installed in the Installed Apps folder and dashboard panels will start to fill automatically.
See our Release Notes changelog for new updates in the app.
To revert the app to a previous version, do the following:
- Select App Catalog.
- In the Search Apps field, search for and then select your app.
- To version down the app, select Revert to < previous version of your app > from the Manage dropdown.
Uninstalling the Amazon Route 53 Resolver Security app (Optional)
To uninstall the app, do the following:
- Select App Catalog.
- In the 🔎 Search Apps field, run a search for your desired app, then select it.
- Click Uninstall.