AWS Security Hub - OCSF

The AWS Security Hub – OCSF app offers a centralized, structured view into your AWS security findings using the Open Cybersecurity Schema Framework (OCSF). This app is designed to help security teams identify threats, track compliance violations, and investigate affected resources with speed and clarity.
With pre-configured dashboards and in-depth visualizations, this app helps you to monitor findings by severity, region, account, and classification. You can assess security trends over time, evaluate cloud resource exposure, and analyze the effectiveness of your cloud security posture across multiple AWS services.
Whether you need to investigate recent security events, track compliance gaps against key industry standards like PCI or NIST, or prioritize remediation by impacted resources, this app provides actionable insights in one place. Designed for both strategic oversight and tactical response, the app streamlines cloud security operations and supports better decision-making across teams.
This app includes built-in monitors. For details on creating custom monitors, refer to Create monitors for AWS Security Hub - OCSF app.
Log types
The AWS Security Hub - OCSF app uses the Security Hub Findings log types.
Sample log message
{
"version": "0",
"id": "994b02ab-3ee4-9576-abcb-6a920op2c085",
"detail-type": "Findings Imported V2",
"source": "aws.securityhub",
"account": "869728294964",
"time": "2025-07-22T03:03:15Z",
"region": "us-east-1",
"resources": [
"1d24e91799652d9e17025b61d94f436b20b515b6f3cd9bda788f48c1db9cf244"
],
"detail": {
"findings": [
{
"activity_id": 2,
"activity_name": "Update",
"category_name": "Findings",
"category_uid": 2,
"class_name": "Detection Finding",
"class_uid": 2004,
"cloud": {
"account": {
"type": "AWS Account",
"type_id": 10,
"uid": "869728294964"
},
"cloud_partition": "aws",
"provider": "AWS",
"region": "us-east-1"
},
"comment": "John's testing",
"count": 264,
"evidences": [
{
"api": {
"operation": "DeleteTrail",
"service": {
"name": "cloudtrail.amazonaws.com"
}
},
"data": {
"affected_resource": {
"AWS::CloudTrail::Trail": "Aws-Observability-e2esumoqeui"
},
"resource_role": "TARGET"
}
}
],
"finding_info": {
"analytic": {
"type": "Rule",
"type_id": 1,
"uid": "b4c71b47fb852d3fc0e99a82fa2841aa"
},
"created_time": 1729766226938,
"created_time_dt": "2024-10-24T10:37:06.938Z",
"desc": "AWS CloudTrail trail Aws-Observability-e2esumoqeui was disabled by cis_automation calling DeleteTrail under unusual circumstances. This can be attackers attempt to cover their tracks by eliminating any trace of activity performed while they accessed your account.",
"first_seen_time": 1729765286000,
"first_seen_time_dt": "2024-10-24T10:21:26.000Z",
"last_seen_time": 1753152734000,
"last_seen_time_dt": "2025-07-22T02:52:14.000Z",
"modified_time": 1753153354272,
"modified_time_dt": "2025-07-22T03:02:34.272Z",
"product": {
"uid": "b4c71b47fb852d3fc0e99a82fa2841aa"
},
"title": "An AWS CloudTrail trail Aws-Observability-e2esumoqeui was disabled.",
"types": [
"Stealth:IAMUser/CloudTrailLoggingDisabled"
],
"uid": "arn:aws:guardduty:us-east-1:869728294630:detector/b4c71b47fb852d3fc0e99a82fa2841aa/finding/06c95f0cfdfd3b579b977e20e9da1aa4",
"uid_alt": "06c95f0cfdfd3b579b977e20e9da1aa4"
},
"metadata": {
"product": {
"name": "GuardDuty",
"uid": "arn:aws:securityhub:us-east-1::productv2/aws/guardduty",
"vendor_name": "AWS"
},
"profiles": [
"cloud",
"datetime"
],
"uid": "1d24e91799652d9e17025b61d94f436b20b515b6f3cd9bda788f48c1db9cf244",
"version": "1.5.0"
},
"remediation": {
"desc": "Please review the remediation guidance provided in the referenced documentation",
"references": [
"https://docs.aws.amazon.com/guardduty/latest/ug/guardduty_finding-types-iam.html#stealth-iam-cloudtrailloggingdisabled"
]
},
"resources": [
{
"cloud_partition": "aws",
"data": {
"access_key_id": "ASIA4U76YS3TB3MEOA3O",
"principal_id": "AROA4U76YS3THXXBAIOOA:aws-go-sdk-1753152318418995274",
"user_name": "cis_automation",
"user_type": "AssumedRole"
},
"name": "cis_automation",
"owner": {
"account": {
"type": "AWS Account",
"type_id": 10,
"uid": "869728294964"
}
},
"region": "us-east-1",
"type": "AWS::IAM::AccessKey",
"uid": "ASIA4U76YS3TEOA3O"
}
],
"severity": "Low",
"severity_id": 2,
"status": "Suppressed",
"status_id": 3,
"time": 1753153354272,
"time_dt": "2025-07-22T03:02:34.272Z",
"type_name": "Detection Finding: Update",
"type_uid": 200402,
"vendor_attributes": {
"severity": "Low",
"severity_id": 2
}
}
]
}
}
Sample query
_sourcecategory="yl/webhook" category_name activity_name
| json "detail.findings[0]" as finding nodrop
| json field=finding "finding_info.uid","finding_info.first_seen_time","finding_info.last_seen_time","finding_info.modified_time", "finding_info.modified_time_dt", "severity","cloud.account.uid","status","compliance.status","finding_info.types","cloud.region","class_name","finding_info.analytic.category","activity_name","metadata.product.name","metadata.product.vendor_name","resources[*]","finding_info.title","remediation.desc","remediation.references[0]","evidences[*].data.resource_role" as finding_id,finding_first_seen_time,finding_last_seen_time,finding_modified_time,finding_info_modified_time_dt,severity,aws_account_id,finding_status,compliance_status,finding_types,cloud_region,class_name,category_name,activity_name,product_name,vendor_name,resources,title,remediation_description,remediation_references,evidences_data_resource_roles nodrop
| topk(1, finding_modified_time) by finding_id
| parse regex field=resources "(?<resource>\{(?:[^\{\}]|\{(?:[^\{\}]|\{[^\{\}]*\})*\})*\})" multi
| json field=resource "type","uid","name","owner.account.uid","region" as resource_type,resource_name,resource_title,resource_account_id,resource_region nodrop
// global filters
| where if ("{{aws_account_id}}" = "*", true, aws_account_id matches "{{aws_account_id}}")
| where if ("{{severity}}" = "*", true, severity matches "{{severity}}")
| where if ("{{finding_status}}" = "*", true, finding_status matches "{{finding_status}}")
| where if ("{{compliance_status}}" = "*", true, compliance_status matches "{{compliance_status}}")
| where if ("{{aws_region}}" = "*", true, cloud_region matches "{{aws_region}}")
| where if ("{{class_name}}" = "*", true, class_name matches "{{class_name}}")
| where if ("{{finding_activity}}" = "*", true, activity_name matches "{{finding_activity}}")
| where if ("{{finding_category}}" = "*", true, category_name matches "{{finding_category}}")
| where if ("{{resource_type}}" = "*", true, resource_type matches "{{resource_type}}")
| where if ("{{resource_name}}" = "*", true, resource_name matches "{{resource_name}}")
// panel specific
| count by finding_id
| count
Set up collection
This integration enables the ingestion of AWS Security Hub findings into Sumo Logic using Amazon EventBridge and a Sumo Logic HTTP Source. It provides a scalable and real-time pipeline: Security Hub > EventBridge > Sumo Logic HTTP Source
Step 1: Create an HTTP Source in Sumo Logic
- To create an HTTP source in Sumo Logic, refer to Configure an HTTP Logs and Metrics Source.
- After creation, copy and save the HTTP Source URL and Source Category for further steps.
Step 2: Configure EventBridge API destination
Follow the below steps to configure the EventBridge API destination:
- Sign in to your AWS Eventbridge Console.
- In the navigation bar, click API destinations.
- Click Create destination.
- Enter a name for the API Destination.
- Provide the HTTP Source URL collected from Step 1.
- Click Create a new connection to create a connection for the API destination.
- Provide a connection name.
- Keep the API Type as Public.
- In the Authorization type select Basic (Username/Password) and add any value of your choice for Username and Password.
Step 3: Create the EventBridge rule
Follow the below steps to create the EventBridge rule:
- Sign in to your AWS Eventbridge Console..
- In the navigation bar, click Rules.
- Set the event source to AWS services and then select Security Hub as the AWS service.
- Select All Events in the Event Type.
- Under Select targets, choose EventBridge API destination.
- Select the API Destination created in Step 2.
- Select Create a new role for this specific resource in the Execution role.
- Click Create to activate the rule.
Once the rule is active, Security Hub findings will automatically be sent to the configured Sumo Logic HTTP source.
Installing the AWS Security Hub - OCSF app
To install the app, do the following:
Next-Gen App: To install or update the app, you must be an account administrator or a user with Manage Apps, Manage Monitors, Manage Fields, Manage Metric Rules, and Manage Collectors capabilities depending upon the different content types part of the app.
- Select App Catalog.
- In the 🔎 Search Apps field, run a search for your desired app, then select it.
- Click Install App.
note
Sometimes this button says Add Integration.
- Click Next in the Setup Data section.
- In the Configure section of your respective app, complete the following fields.
- Field Name. If you already have collectors and sources set up, select the configured metadata field name (eg _sourcecategory) or specify other custom metadata (eg: _collector) along with its metadata Field Value.
- Click Next. You will be redirected to the Preview & Done section.
Post-installation
Once your app is installed, it will appear in your Installed Apps folder, and dashboard panels will start to fill automatically.
Each panel slowly fills with data matching the time range query received since the panel was created. Results will not immediately be available but will be updated with full graphs and charts over time.
Viewing AWS Security Hub - OCSF dashboards
All dashboards have a set of filters that you can apply to the entire dashboard. Use these filters to drill down and examine the data to a granular level.
- You can change the time range for a dashboard or panel by selecting a predefined interval from a drop-down list, choosing a recently used time range, or specifying custom dates and times. Learn more.
- You can use template variables to drill down and examine the data on a granular level. For more information, see Filtering Dashboards with Template Variables.
- Most Next-Gen apps allow you to provide the scope at the installation time and are comprised of a key (
_sourceCategoryby default) and a default value for this key. Based on your input, the app dashboards will be parameterized with a dashboard variable, allowing you to change the dataset queried by all panels. This eliminates the need to create multiple copies of the same dashboard with different queries.
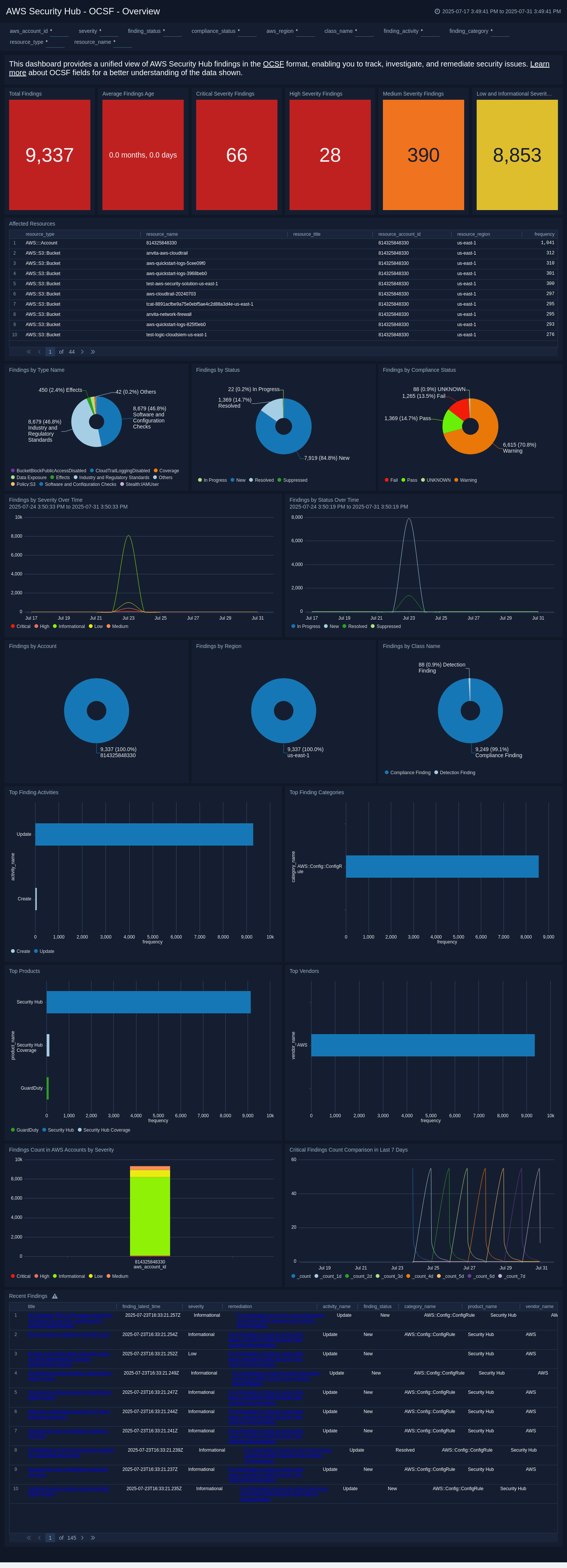
Overview
The AWS Security Hub - OCSF - Overview dashboard delivers a broad, real-time snapshot of your AWS Security Hub findings. It provides high-level insight into alert volume, severity distribution, account-level risk, and compliance status across your AWS environment.
These dashboard panels help you to track findings over time, analyze spikes in critical issues, and assess which accounts or regions are experiencing the most significant activity. You can also drill into findings by classification, category, type, or vendor to understand threat sources and affected services.
Additionally, this dashboard highlights recently discovered findings and affected resources, helping teams quickly spot emerging risks. Use this dashboard to stay informed of your overall security posture and to surface high-priority issues that demand immediate attention.
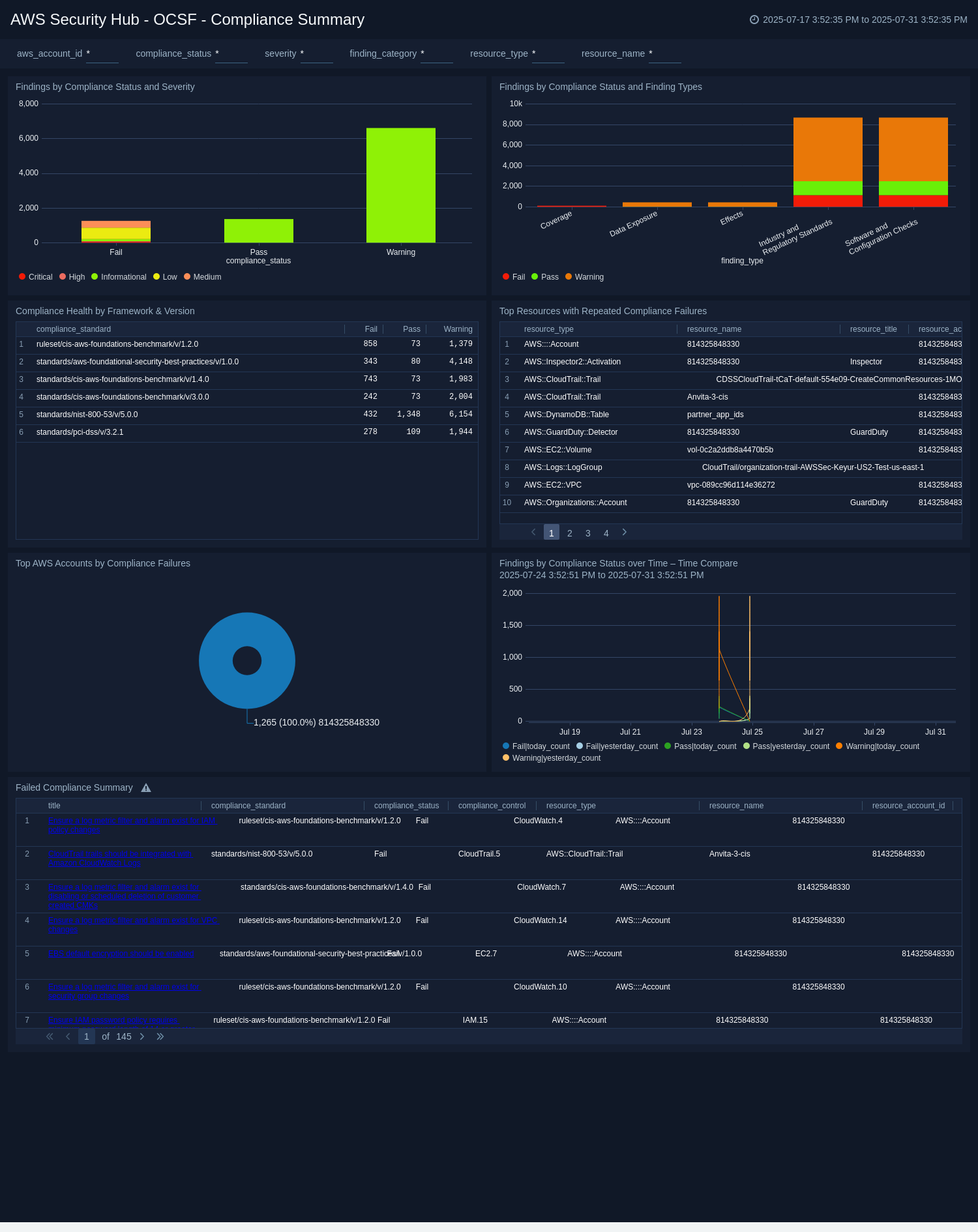
Compliance Summary
The AWS Security Hub - OCSF - Compliance Summary dashboard provides a focused analysis of your AWS compliance posture, aggregating finding data across key compliance standards. The dashboard highlights the failures that occurs across accounts, resources, and time, providing teams the visibility needed to assess audit readiness and take corrective action.
It surfaces trends in compliance violations, enabling you to monitor status changes, detect regressions, and evaluate severity distribution. You can also identify the top misconfigured resources and non-compliant AWS accounts, helping prioritize efforts to improve adherence to security frameworks.
This dashboard is ideal for security and compliance teams who need to ensure ongoing alignment with internal policies and external regulatory standards.
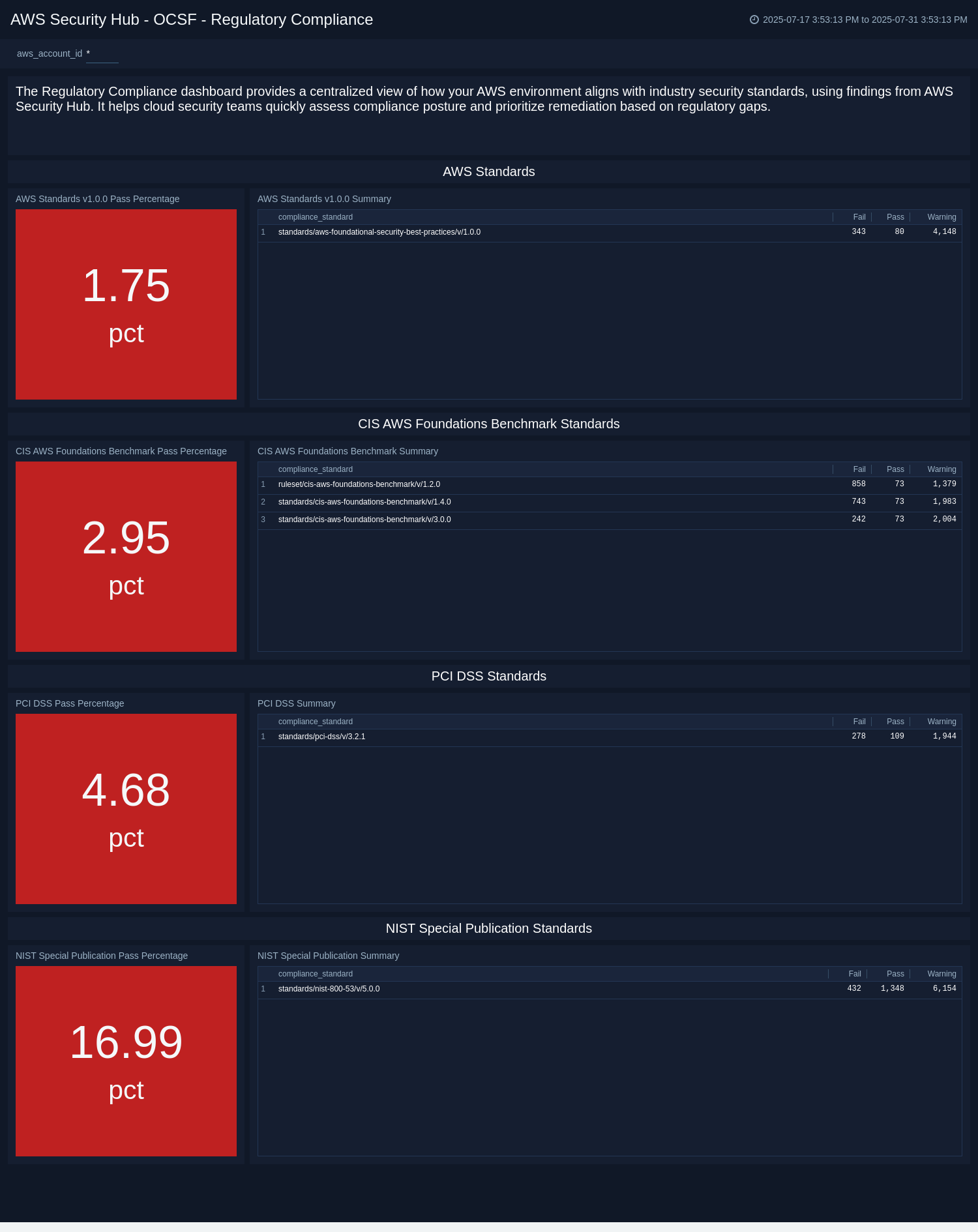
Regulatory Compliance
The AWS Security Hub - OCSF - Regulatory Compliance dashboard presents an in-depth view of your organization's alignment with major cloud security benchmarks and compliance standards, such as AWS Foundational Security Best Practices, CIS Benchmarks, NIST publications, and PCI DSS.
The dashboard shows pass percentages and summary details for each standard, allowing teams to compare compliance levels across frameworks. With this level of granularity, security and governance teams can pinpoint specific areas of misalignment, measure improvement over time, and tailor remediation efforts by standard.
Use this dashboard to assess policy adherence in detail, validate control coverage, and support audit processes with clearly segmented compliance insights.
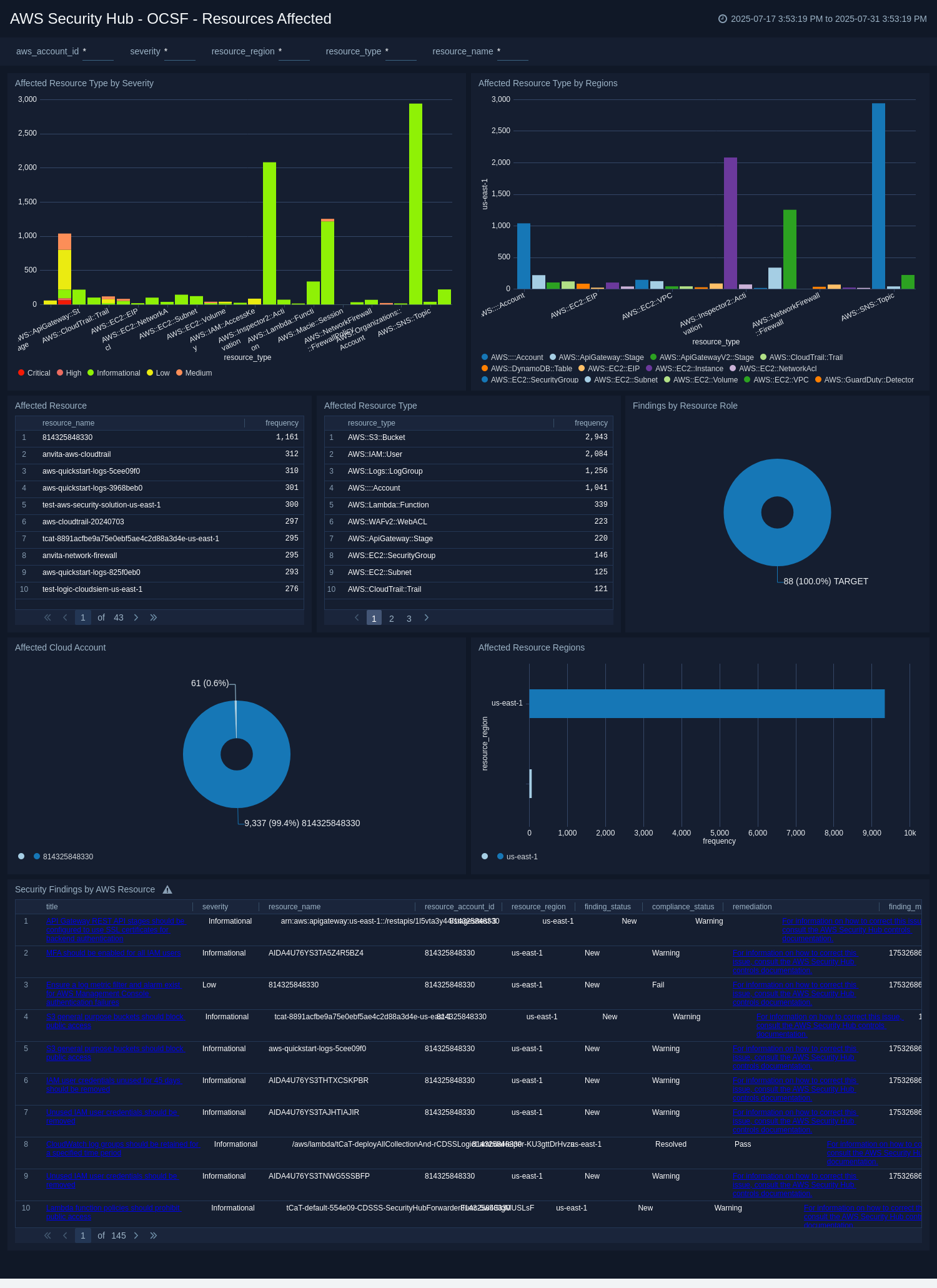
Resources Affected
The AWS Security Hub - OCSF - Resources Affected dashboard helps security teams understand which AWS resources are impacted by security findings and where those resources are distributed across cloud accounts and regions.
By organizing data by resource type, severity, and geography, this dashboard helps prioritize remediation based on criticality and business impact. You can identify top affected resource names, evaluate role-based exposure, and explore findings across various infrastructure layers.
With this information, teams can quickly assess the blast radius of an incident, uncover systemic misconfigurations, and take action to protect their most sensitive and critical cloud assets.
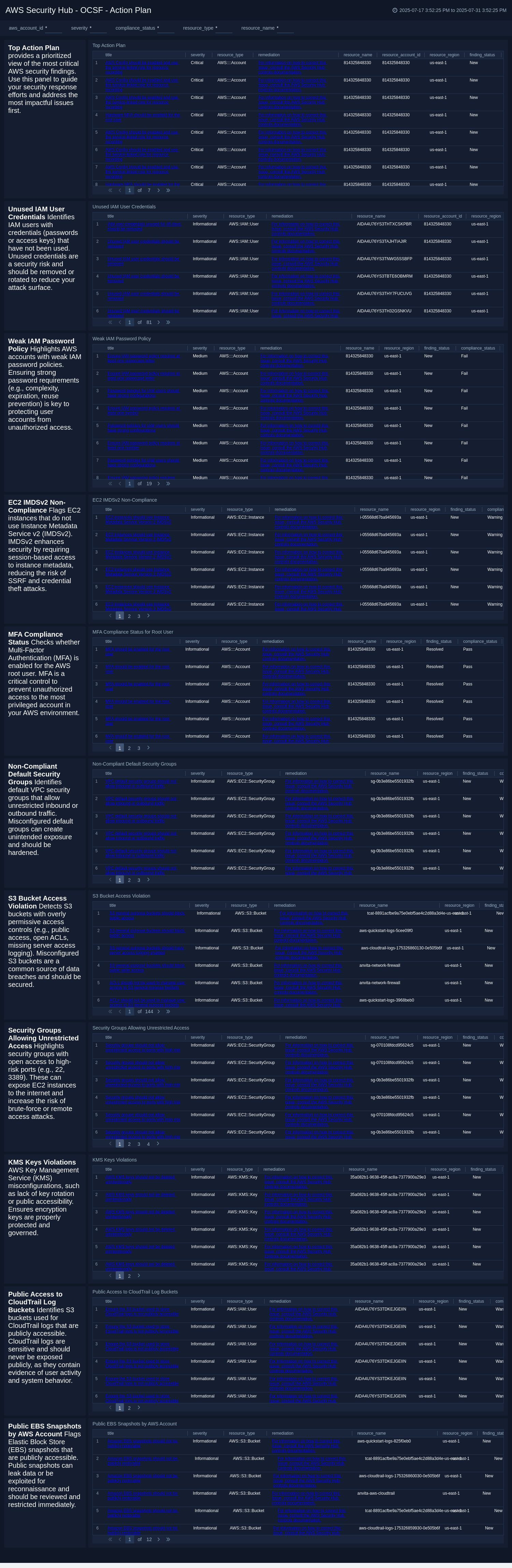
Action Plan
The AWS Security Hub - OCSF - Action Plan dashboard provides a tactical view into common misconfigurations and high-risk behaviors across your AWS environment. It surfaces key remediation opportunities such as exposed credentials, weak password policies, non-compliant security group rules, public access violations, and critical S3 and EC2 misconfigurations.
This dashboard helps operationalize findings by translating alerts into prioritized action items. Security teams can easily pinpoint unused credentials, monitor MFA adoption, and address overly permissive network settings or encryption gaps.
Use this dashboard to drive remediation workflows, reduce the attack surface, and continuously improve your cloud security hygiene through targeted action.
Create monitors for AWS Security Hub - OCSF app
From your App Catalog:
- From the Sumo Logic navigation, select App Catalog.
- In the Search Apps field, search for and then select your app.
- Make sure the app is installed.
- Navigate to What's Included tab and scroll down to the Monitors section.
- Click Create next to the pre-configured monitors. In the create monitors window, adjust the trigger conditions and notifications settings based on your requirements.
- Scroll down to Monitor Details.
- Under Location click on New Folder.
note
By default, monitor will be saved in the root folder. So to make the maintenance easier, create a new folder in the location of your choice.
- Enter Folder Name. Folder Description is optional.
tip
Using app version in the folder name will be helpful to determine the versioning for future updates.
- Click Create. Once the folder is created, click on Save.
AWS Security Hub - OCSF alerts
| Name | Description | Trigger Type (Critical / Warning / MissingData) | Alert Condition |
|---|---|---|---|
Critical Severity Findings | This alert is triggered when a finding with critical severity is detected, indicating a high-impact threat that requires immediate attention and remediation. | Critical | Count > 0 |
High Severity Findings | This alert is triggered when a high-severity finding is generated, signaling a significant security issue that should be investigated promptly. | Critical | Count > 0 |
S3 Bucket Access Violation | This alert is triggered when a finding indicates that an S3 bucket lacks proper access controls or configurations that may expose data to unauthorized access. Alert is activated when the finding matches any of the following:
These misconfigurations significantly increase the risk of data exposure or unauthorized access to sensitive resources. | Critical | Count > 0 |
Security Groups Allowing Unrestricted Access | This alert is triggered when a finding identifies overly permissive security group rules that could expose cloud resources to unauthorized access. Alert is activated when the finding matches any of the following:
These configurations can create open attack surfaces and significantly increase the likelihood of brute-force attacks, lateral movement, or unauthorized remote access. | Critical | Count > 0 |
Public Access Violations | This alert is triggered when publicly accessible cloud resources, such as S3 buckets, CloudTrail log storage, or KMS keys are detected. These cloud resources pose a significant risk of data leakage or unauthorized access. Alert is activated when the finding matches any of the following:
These above findings highlight the misconfigurations that can expose sensitive data or services to the public internet and should be remediated promptly. | Critical | Count > 0 |
Upgrade/Downgrade the AWS Security Hub - OCSF app (Optional)
To update the app, do the following:
Next-Gen App: To install or update the app, you must be an account administrator or a user with Manage Apps, Manage Monitors, Manage Fields, Manage Metric Rules, and Manage Collectors capabilities depending upon the different content types part of the app.
- Select App Catalog.
- In the Search Apps field, search for and then select your app.
Optionally, you can identify apps that can be upgraded in the Upgrade available section. - To upgrade the app, select Upgrade from the Manage dropdown.
- If the upgrade does not have any configuration or property changes, you will be redirected to the Preview & Done section.
- If the upgrade has any configuration or property changes, you will be redirected to the Setup Data page.
- In the Configure section of your respective app, complete the following fields.
- Field Name. If you already have collectors and sources set up, select the configured metadata field name (eg _sourcecategory) or specify other custom metadata (eg: _collector) along with its metadata Field Value.
- Click Next. You will be redirected to the Preview & Done section.
Post-update
Your upgraded app will be installed in the Installed Apps folder and dashboard panels will start to fill automatically.
See our Release Notes changelog for new updates in the app.
To revert the app to a previous version, do the following:
- Select App Catalog.
- In the Search Apps field, search for and then select your app.
- To version down the app, select Revert to < previous version of your app > from the Manage dropdown.
Uninstalling the AWS Security Hub - OCSF app (Optional)
To uninstall the app, do the following:
- Select App Catalog.
- In the 🔎 Search Apps field, run a search for your desired app, then select it.
- Click Uninstall.