Azure Virtual Network

Azure Virtual Network is a service that provides the fundamental building block for your private network in Azure enabling many types of Azure resources to securely communicate with each other, using the internet, and on-premises networks. This integration helps in monitoring the outgoing and incoming traffic flows, dropped packets, bandwidth consumption, and verifying network isolation and compliance.
Logs and metric types
For Azure Virtual Network, you can collect the following logs and metrics:
-
Virtual network flow logs. It provides ingress and egress IP traffic flow with the following information:
- Inbound and Outbound flows per Rule
- NIC and traffic flow
- 5-tuple information with respect to flow (Source/Destination IP and Port, Protocol)
- Allowed/Denied traffic flow.
- Encryption status of your traffic
For more information, refer to the virtual flow logs documentations.
-
Platform Metrics for Azure Virtual Network. These metrics are available in Microsoft.Network/virtualNetworks namespace.
Sample log messages
{
"acl_id": "/subscriptions/c088dd12-d692-42ad-a4b6-9a542d12ad2a/resourceGroups/hpalvnapp/providers/Microsoft.Network/networkSecurityGroups/MyLowCostVM-nsg",
"bytes_sent_dest_to_src": "2572",
"bytes_sent_src_to_dest": "2352",
"category": "FlowLogFlowEvent",
"dest_IP": "10.2.0.4",
"dest_port": "22",
"event_name": "FlowLogFlowEvent",
"flowLogGUID": "b003d9f1-852e-419f-bed2-ec2d166d05e2",
"flow_direction": "I",
"flow_encryption_status": "NX",
"flow_log_resource_id": "/SUBSCRIPTIONS/C088DD12-D692-42AD-A4B6-9A542D12AD2A/RESOURCEGROUPS/NETWORKWATCHERRG/PROVIDERS/MICROSOFT.NETWORK/NETWORKWATCHERS/NETWORKWATCHER_EASTUS/FLOWLOGS/MYLOWCOSTVM837_Z1-HPALVNAPP-FLOWLOG",
"flow_state": "E",
"mac": "000D3A130BFE",
"num_packets_sent_dest_to_src": "11",
"num_packets_sent_src_to_dest": "11",
"protocol": "6",
"rule_name": "UserRule_AllowMyIpAddressCustom8080Inbound",
"src_ip": "91.118.39.74",
"src_port": "55304",
"target_resource_id": "/subscriptions/c088dd12-d692-42ad-a4b6-9a542d12ad2a/resourceGroups/hpalvnapp/providers/Microsoft.Network/networkInterfaces/mylowcostvm837_z1",
"time": "1737500459279",
"version": 4
}
Sample queries
_sourceCategory=Azure/VirtualNetworkFlow/Logs
| json field=_raw "rule_name"
| json field=_raw "target_resource_id"
| json field=_raw "event_name"
| json field=_raw "mac"
| json field=_raw "src_ip"
| json field=_raw "dest_IP"
| json field=_raw "dest_port"
| json field=_raw "protocol"
| if(protocol="T","TCP", protocol) as protocol
| if(protocol="U","UDP", protocol) as protocol
| parse regex field=target_resource_id"(?<NSG>[\w-_.]+)$"
| json field=_raw "src_port"
| json field=_raw "flow_direction"
| json field=_raw "flow_state" as traffic_a_d
| timeslice 1h
|where if ("*" = "*", true, protocol matches "*") AND if ("*" = "*", true, src_ip matches "*") AND if ("*" = "*", true, mac matches "*") AND if ("*" = "*", true, dest_port matches "*") AND if ("*" = "*", true, traffic_a_d matches "*") AND if ("*" = "*", true, dest_ip matches "*") AND if ("*" = "*", true, rule_name matches "*") AND if ("*" = "*", true, flow_direction matches "*") AND if ("*" = "*", true, event_name matches "*") AND if ("*" = "*", true, nsg matches "*")
|count by rule_name,_timeslice
| transpose row _timeslice column rule_name
Setup
Azure service sends monitoring data to Azure Monitor, which can then stream data to Eventhub. Sumo Logic supports:
- Virtual Network Flow Logs collection from Storage Account using our Collect Logs from Azure Blob Storage integration.
- Activity Logs collection from Azure Monitor using our Azure Event Hubs source. It is recommended to create a separate source for activity logs. If you are already collecting these logs, you can skip this step.
- Metrics collection using Azure Metrics Source.
You must explicitly enable diagnostic settings and network flow logs for each Virtual Network you want to monitor. You can forward metrics to the same event hub provided they satisfy the limitations and permissions as described here.
When you configure the event hubs source or HTTP source, plan your source category to ease the querying process. A hierarchical approach allows you to make use of wildcards. For example: Azure/VirtualNetwork/Metrics and Azure/VirtualNetwork/Logs.
Configure collector
Create a hosted collector if not already configured and tag the tenant_name field. You can get the tenant name using the instructions here. Make sure you create the required sources in this collector. 
Configure metrics collection
To set up the Azure Metrics source in Sumo Logic, refer to Azure Metrics Source.
Configure logs collection
Configuration requirements
Before you begin configuring the Virtual Network Flow Log collection, make sure the following environment prerequisites are met:
- Your Storage Account must be of type General-purpose v2 or Blob storage.
- Your Network Security Group and Storage Account should be in the same resource location.
- You also need to have Microsoft Authorization/role Assignments/write permissions, so they should be a "User Access Administrator" or "Owner".
- Location: The storage account must be in the same region as the virtual network.
- Subscription: The storage account must be in the same subscription of the virtual network or in a subscription associated with the same Microsoft Entra tenant of the virtual network's subscription.
- Performance tier: The storage account must be standard. Premium storage accounts aren't supported.
- Self-managed key rotation: If you change or rotate the access keys to your storage account, virtual network flow logs stop working. To fix this problem, you must disable and then re-enable virtual network flow logs.
Resource group names should not contain underscores (_).
Step 1: Configure Azure Storage Account
In this step, you'll configure a storage account to export monitoring data for your Azure service. The storage account must be a General-purpose v2 (GPv2) storage account. If you have a storage account with a container that you want to use for this purpose, make a note of its resource group, storage account name, and container name, and proceed to step 2.
To configure an Azure storage account, do the following:
-
Create a new storage account General-purpose v2 (GPv2) storage account. For instructions, see Create a storage account in Azure help.
-
Create a container(Optional) all services in Azure create containers automatically. This step is needed only when you are exporting custom logs in some container.
- In the Azure portal, navigate to the storage account you just created (in the previous step).
- Select Blobs under Blob Service.
- Select + Container,
- Enter the Name
- Select Private for the Public Access Level.
- Click OK.
Make a note of the container name. You will need to supply it later. By default, the flow logs are in
insights-logs-flowlogfloweventcontainer. If you have a storage account that you want to use for this purpose, make a note of its resource group, and storage account name, then proceed to step 2.
Step 2: Configure an HTTP Source
This section demonstrates how to configure an HTTP source to receive logs from the Azure function.
To configure an HTTP source for Azure, do the following:
- Select a hosted collector where you want to configure the HTTP source. If desired, create a new hosted collector, as described on Configure a Hosted Collector.
- Configure an HTTP source, as described on HTTP Logs and Metrics Source. Make a note of the URL for the source, you will need it in the next step.
- In Advanced Options for Logs, under Timestamp Format, click Specify a format and enter the following:
- Specify Format as epoch
- Specify Timestamp locator as
\"time\": (.*),
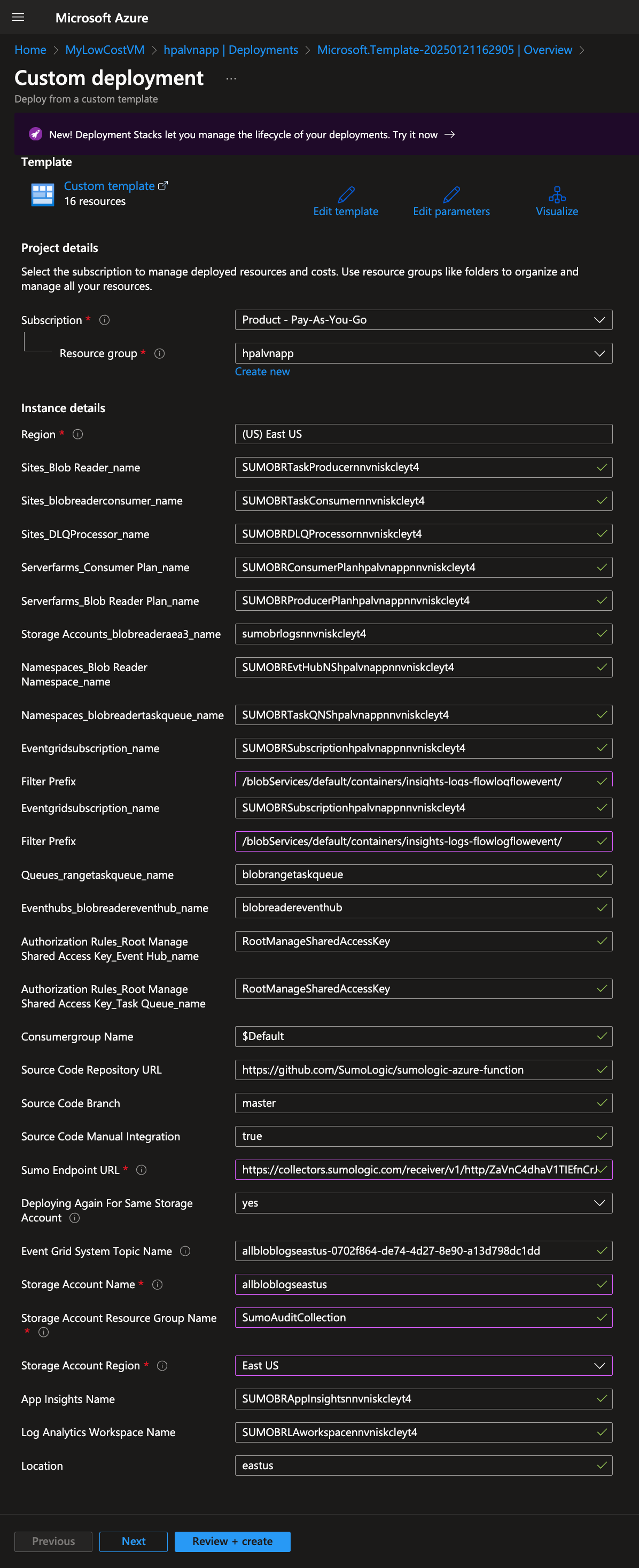
Step 3: Configure Azure Resources using ARM template
To deploy the ARM template-based Blob Storage collection, refer to step 3 of Collect Logs from Azure Blob Storage(block blobs). If you want to collect only flow logs from the storage account, you can add the filter /blobServices/default/containers/insights-logs-flowlogflowevent/.
Step 4: Enable Virtual Network flow logs via the Azure Portal
Follow the steps detailed in the Microsoft Azure Virtual Network documentation to enable the flow logs to point to the storage account you configured in the Configure Azure Storage Account section. You can select any target resources (available options are: Virtual network, Subnet, and Network interface) based on your requirements.

If you have multiple virtual networks, you can configure virtual network flow logs using a built-in policy for each location and subscriptions.
Activity logs (optional)
To collect activity logs, follow the instructions here. If you are already collecting activity logs for a subscription, you can skip this step.
Since this source includes logs from multiple regions, do not tag it with the location tag.
In order to find virtual networks without any flow log resource, you can audit flow logs configuration for virtual networks using a built-in policy.
Installing the Azure Virtual Network app
Now that you have set up data collection, install the Azure Virtual Network Sumo Logic app to use the pre-configured dashboards that provide visibility into your environment for real-time analysis of overall usage.
To install the app, do the following:
Next-Gen App: To install or update the app, you must be an account administrator or a user with Manage Apps, Manage Monitors, Manage Fields, Manage Metric Rules, and Manage Collectors capabilities depending upon the different content types part of the app.
- Select App Catalog.
- In the 🔎 Search Apps field, run a search for your desired app, then select it.
- Click Install App.
note
Sometimes this button says Add Integration.
- Click Next in the Setup Data section.
- In the Configure App section of your respective app, complete the following field.
- Index. Specify value for _index if the collection is configured with custom partition. Learn more. Default value is set to
sumologic_default(default partition)
- Index. Specify value for _index if the collection is configured with custom partition. Learn more. Default value is set to
- Click Next. You will be redirected to the Preview & Done section.
Post-installation
Once your app is installed, it will appear in your Installed Apps folder, and dashboard panels will start to fill automatically.
Each panel slowly fills with data matching the time range query received since the panel was created. Results will not immediately be available but will be updated with full graphs and charts over time.
As part of the app installation process, the following fields will be created by default:
tenant_name. This field is tagged at the collector level. You can get the tenant name using the instructions here.location. The region the resource name belongs to.subscription_id. ID associated with a subscription where the resource is present.resource_group. The resource group name where the Azure resource is present.provider_name. Azure resource provider name (for example, Microsoft.Network).resource_type. Azure resource type (for example, storage accounts).resource_name. The name of the resource (for example, storage account name).service_type. Type of the service that can be accessed with an Azure resource.service_name. Services that can be accessed with an Azure resource (for example, in Azure Container Instances the service is Subscriptions).
Also FER AzureVirtualNetworkTargetResourceIdExtractionFER will be created as part of the app installation process itself.
Viewing the Azure Virtual Network app dashboards
All dashboards have a set of filters that you can apply to the entire dashboard. Use these filters to drill down and examine the data to a granular level.
- You can change the time range for a dashboard or panel by selecting a predefined interval from a drop-down list, choosing a recently used time range, or specifying custom dates and times. Learn more.
- You can use template variables to drill down and examine the data on a granular level. For more information, see Filtering Dashboards with Template Variables.
- Many of the Next-Gen apps allow you to provide the Index at the installation time and a default value for this key (sumologic_default). Based on your input, the app dashboards will be parameterized with a dashboard variable, allowing you to change the data partition queried by all panels. This restricts the query scope of all the dashboard queries to a specific data partition.
Overview
Azure Virtual Network - Overview dashboard provides details on network traffic flows, including accepted and rejected connections, geographical distribution, and data access patterns across different network boundaries.
Use this dashboard to:
- Monitor the geographical distribution of source and destination traffic to identify unusual patterns or potential security threats.
- Analyze the accepted to rejected flows ratio, and investigate the top rejected destination ports to troubleshoot connectivity issues.
- Compare the current network usage with historical averages to detect anomalies or assess capacity planning needs.
- Examine data access across borders, both North-South and East-West, to optimize network segmentation and security policies.
- Identify top resources by bytes sent and the top TCP destination ports to prioritize network optimization efforts.

Accepted Traffic Flow
Azure Virtual Network - Accepted Traffic Flow dashboard provides details on incoming and outgoing network traffic, packet flows, and security group rules applied to traffic flows.
Use this dashboard to:
- Visualize and compare incoming and outgoing traffic patterns across various geographical locations to identify potential network bottlenecks or unusual activity.
- Monitor accepted flow traffic by resource name over time to detect spikes or drops in network usage, which could indicate performance issues or security concerns.
- Analyze the top accepted source and destination IP addresses and ports to understand common traffic patterns and potentially identify unauthorized or suspicious connections.
- Review accepted flow traffic by resource name and Access Control List (ACL) to ensure that network security group rules are properly configured and functioning as intended.

Administrative Operations
Azure Virtual Network - Administrative Operations dashboard provides details on various administrative actions performed on Azure Virtual Network resources, including their operation types, status, and associated errors.
Use this dashboard to:
- Monitor the distribution of operation types (Read, Write, Delete) to understand the most common actions performed on your virtual network resources.
- Analyze the distribution of operation statuses to identify potential issues, focusing on failures and their root causes.
- Track user and application activity by examining the breakdown of operations per entity, helping to detect unusual patterns or unauthorized access.
- Investigate specific errors by reviewing the top operations causing issues, enabling swift troubleshooting and resolution.
- Audit recent write and delete operations to ensure compliance with organizational policies and detect any suspicious activities.

Policy and Recommendations
Azure Virtual Network - Policy and Recommendations dashboard provides details on policy events and recommendations for Azure Virtual Networks.
Use this dashboard to:
- Monitor and analyze both successful and failed policy events across your Azure Virtual Network resources to ensure compliance and security.
- Identify potential security risks by correlating failed policy events with specific resource groups and locations, enabling targeted mitigation.
- Review and implement recommendations to enhance the operational excellence and security of your Azure Virtual Network infrastructure.

DDOS Protection
Azure Virtual Network - DDOS Protection dashboard provides details on DDoS attacks and packet rates for virtual networks in Azure. Use this dashboard to:
- Monitor and track the frequency of DDoS attacks on your virtual networks over time to assess ongoing threats.
- Analyze the overall packet rate during DDoS attacks to gauge the scale and impact of the attack.
- Compare TCP and UDP packet rates during an attack to determine the attack type, allowing you to tailor your mitigation strategies more effectively.

Denied Traffic Flow
Azure Virtual Network - Denied Traffic Flow dashboard provides details on blocked network traffic across your Azure virtual networks, including geographical distribution, resource-specific denials, and encryption status.
Use this dashboard to:
- Identify geographical hotspots of denied traffic to pinpoint potential security threats or misconfigurations within specific regions.
- Analyze denied traffic patterns by subnet, virtual network, and network interface to refine your network security group rules and access control lists.
- Monitor encryption-related traffic denials to ensure proper implementation of encryption policies across your virtual network.
- Correlate spikes in denied traffic flow with specific source and destination IP addresses to investigate potential security incidents.

Create monitors for Azure Virtual Network
From your App Catalog:
- From the Sumo Logic navigation, select App Catalog.
- In the Search Apps field, search for and then select your app.
- Make sure the app is installed.
- Navigate to What's Included tab and scroll down to the Monitors section.
- Click Create next to the pre-configured monitors. In the create monitors window, adjust the trigger conditions and notifications settings based on your requirements.
- Scroll down to Monitor Details.
- Under Location click on New Folder.
note
By default, monitor will be saved in the root folder. So to make the maintenance easier, create a new folder in the location of your choice.
- Enter Folder Name. Folder Description is optional.
tip
Using app version in the folder name will be helpful to determine the versioning for future updates.
- Click Create. Once the folder is created, click on Save.
Azure Virtual Network alerts
These alerts are metric based and will work for all Virtual Networks.
| Alert Name | Description | Alert Condition | Recover Condition |
|---|---|---|---|
Azure Virtual Network - Under DDoS attack | This alert is triggered when maximum DDoS attack count is greater than 1.0785. | Count > 1.0785 | Count < = 1.0785 |
Upgrade/Downgrade the Azure Virtual Network app (optional)
To update the app, do the following:
Next-Gen App: To install or update the app, you must be an account administrator or a user with Manage Apps, Manage Monitors, Manage Fields, Manage Metric Rules, and Manage Collectors capabilities depending upon the different content types part of the app.
- Select App Catalog.
- In the Search Apps field, search for and then select your app.
Optionally, you can identify apps that can be upgraded in the Upgrade available section. - To upgrade the app, select Upgrade from the Manage dropdown.
- If the upgrade does not have any configuration or property changes, you will be redirected to the Preview & Done section.
- If the upgrade has any configuration or property changes, you will be redirected to the Setup Data page.
- In the Configure section of your respective app, complete the following fields.
- Field Name. If you already have collectors and sources set up, select the configured metadata field name (eg _sourcecategory) or specify other custom metadata (eg: _collector) along with its metadata Field Value.
- Click Next. You will be redirected to the Preview & Done section.
Post-update
Your upgraded app will be installed in the Installed Apps folder and dashboard panels will start to fill automatically.
See our Release Notes changelog for new updates in the app.
To revert the app to a previous version, do the following:
- Select App Catalog.
- In the Search Apps field, search for and then select your app.
- To version down the app, select Revert to < previous version of your app > from the Manage dropdown.
Uninstalling the Azure Virtual Network app (optional)
To uninstall the app, do the following:
- Select App Catalog.
- In the 🔎 Search Apps field, run a search for your desired app, then select it.
- Click Uninstall.
Troubleshooting
Metrics collection via Azure Metrics Source
To troubleshoot metrics collection via Azure Metrics Source, follow the instructions in Troubleshooting Azure Metrics Source.
App installation failed - Content Error - Invalid Field Extraction Rule
This error occurs if the app being installed attempts to create an FER by a name (AzureVirtualNetworkTargetResourceIdExtractionFER) which already exists in the org. This FER could have been created manually and is creating conflict with current app installation flow.
To resolve the issue, rename or delete the existing FER (AzureVirtualNetworkTargetResourceIdExtractionFER) and reinstall the app.