PagerDuty V3

The Sumo Logic App for PagerDuty V3 collects incident messages from your PagerDuty account via a webhook, and displays incident data in pre-configured Dashboards that allow you to monitor and analyze the activity of your PagerDuty account and Services. The Sumo Logic App for PagerDuty V3 uses Webhooks V3, to provide enhanced context for alert object models.
Collect Logs for PagerDuty V3
This section provides instructions for configuring a Sumo Logic Hosted Collector and HTTP Source to create a PagerDuty Webhook V3, to collect PagerDuty events. Click a link to jump to a topic:
- Event types
- Log example
- Sample Queries
- Configure a Sumo Logic Collector and Source
- Create a PagerDuty V3 Webhook
Event types
The Sumo Logic App for PagerDuty V3 ingests PagerDuty incident Webhooks V3 messages, that are triggered by events that occur in your PagerDuty account and Services.
For more information on the incident messages supported in Webhooks V3, see the PagerDuty documentation.
Sample log messages
For examples of incident.triggered, incident.acknowledged and incident.resolved log messages, see the PagerDuty Webhooks V3 Examples page.
Sample queries
The following Top Altering Services query is shown on the PagerDuty V3 - Overview dashboard.
_sourceCategory = Labs/pagerduty_v3 "incident.triggered"
| json "event.event_type","event.data","event.data.created_at" as event,incident,created_on nodrop
| json field=incident "id", "number", "escalation_policy.summary", "service.summary", "status", "title", "urgency", "teams[*].summary", "assignees[*]" as incident_id, incident_number, escalation_policy_name, alertedBy_service, incident_status, incident_title, incident_urgency, incident_team_involved, assignee nodrop
| parse regex field=assignee "summary\":\"(?<assigned_user>.+?)\"" multi nodrop
| alertedBy_service as impacted_service
| where event = "incident.triggered" and impacted_service matches "*" and incident_number matches "*" and incident_status matches "*" and incident_title matches "*" and incident_urgency matches "*"
| count by alertedBy_service
| order by _count
Configure a Sumo Logic Collector and Source
A Hosted Collector is not installed on a local system in your deployment. Instead, Sumo Logic hosts the Collector and its Sources in AWS. With a Hosted Collector, you can create Sources to collect data from various services. A single Hosted Collector can be configured with any number of Sources.
An HTTP Source is an endpoint for receiving log and metric data uploaded to a unique URL generated for the Source. The URL securely encodes the Collector and Source information. You can add as many HTTP Logs and Metrics Sources as you'd like to a single Hosted Collector.
To configure Hosted Collector and HTTP Source, do the following:
- Sign in to Sumo Logic.
- Follow the instructions for configuring a Hosted Collector.
- Follow the instructions for configuring an HTTP Source.
Make sure to save the HTTP Source Address URL. You will be asked for this Endpoint URL when you configure the PagerDuty Webhook in the following procedure.
Create a PagerDuty V3 Webhook
Using PagerDuty with Webhooks V3, you receive HTTP callbacks when incident events occur in your PagerDuty account. Details about the events are then sent via HTTP to a URL that you specify.
To create a PagerDuty V3 Webhook, do the following:
- Log in to your PagerDuty account.
- Navigate to Integrations Generic Webhooks (v3).
- Click New Webhook.
- Configure your webhook:
- Enter the HTTP Source Address URL as the Webhook URL.
- For Scope Type, select Service, Team or Account based on your preferences.
- For Scope, select the desired service or team.
- Enter a Description.
- For Event Subscription, select which events you want to send a webhook.
- Click Add Webhook.
For more information, see https://support.pagerduty.com/docs/webhooks.
In the next section, install the Sumo Logic App for PagerDuty V3.
Installing the PagerDuty V3 App
To install the app, do the following:
Next-Gen App: To install or update the app, you must be an account administrator or a user with Manage Apps, Manage Monitors, Manage Fields, Manage Metric Rules, and Manage Collectors capabilities depending upon the different content types part of the app.
- Select App Catalog.
- In the 🔎 Search Apps field, run a search for your desired app, then select it.
- Click Install App.
note
Sometimes this button says Add Integration.
- Click Next in the Setup Data section.
- In the Configure section of your respective app, complete the following fields.
- Field Name. If you already have collectors and sources set up, select the configured metadata field name (eg _sourcecategory) or specify other custom metadata (eg: _collector) along with its metadata Field Value.
- Click Next. You will be redirected to the Preview & Done section.
Post-installation
Once your app is installed, it will appear in your Installed Apps folder, and dashboard panels will start to fill automatically.
Each panel slowly fills with data matching the time range query received since the panel was created. Results will not immediately be available but will be updated with full graphs and charts over time.
Viewing PagerDuty V3 Dashboards
All dashboards have a set of filters that you can apply to the entire dashboard. Use these filters to drill down and examine the data to a granular level.
- You can change the time range for a dashboard or panel by selecting a predefined interval from a drop-down list, choosing a recently used time range, or specifying custom dates and times. Learn more.
- You can use template variables to drill down and examine the data on a granular level. For more information, see Filtering Dashboards with Template Variables.
- Most Next-Gen apps allow you to provide the scope at the installation time and are comprised of a key (
_sourceCategoryby default) and a default value for this key. Based on your input, the app dashboards will be parameterized with a dashboard variable, allowing you to change the dataset queried by all panels. This eliminates the need to create multiple copies of the same dashboard with different queries.
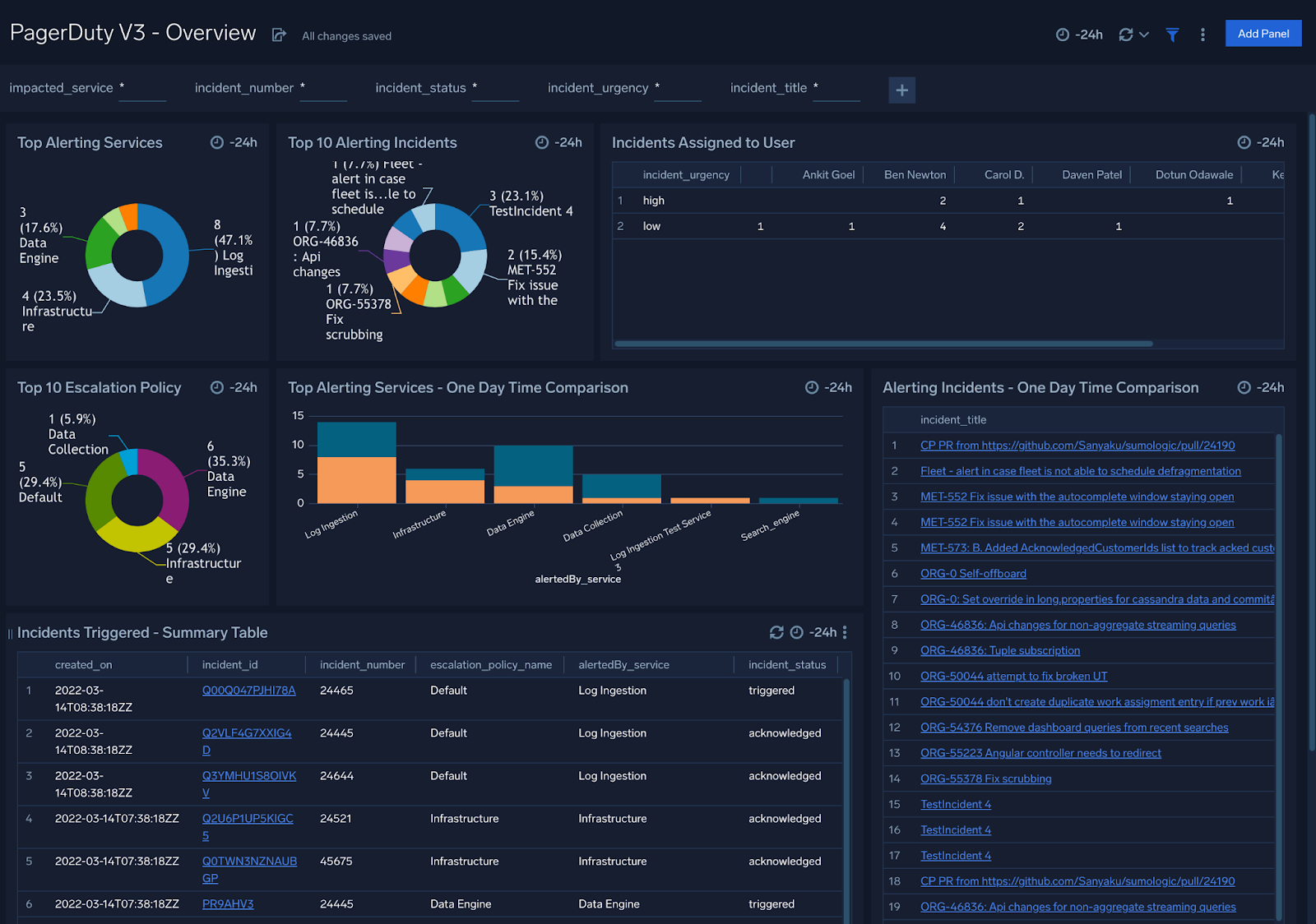
Overview
PagerDuty V3 - Overview Dashboard provides a high-level view of top alerts, triggered incidents summary, as well as a breakdown of per-user incident assignments and comparisons over a specified time interval.
Use this dashboard to:
- Review the services, incidents and policies that are causing the most alerts.
- Analyze detailed information on incidents using the Incident Summary panel.
- Drill down to examine data on a granular level with filters.
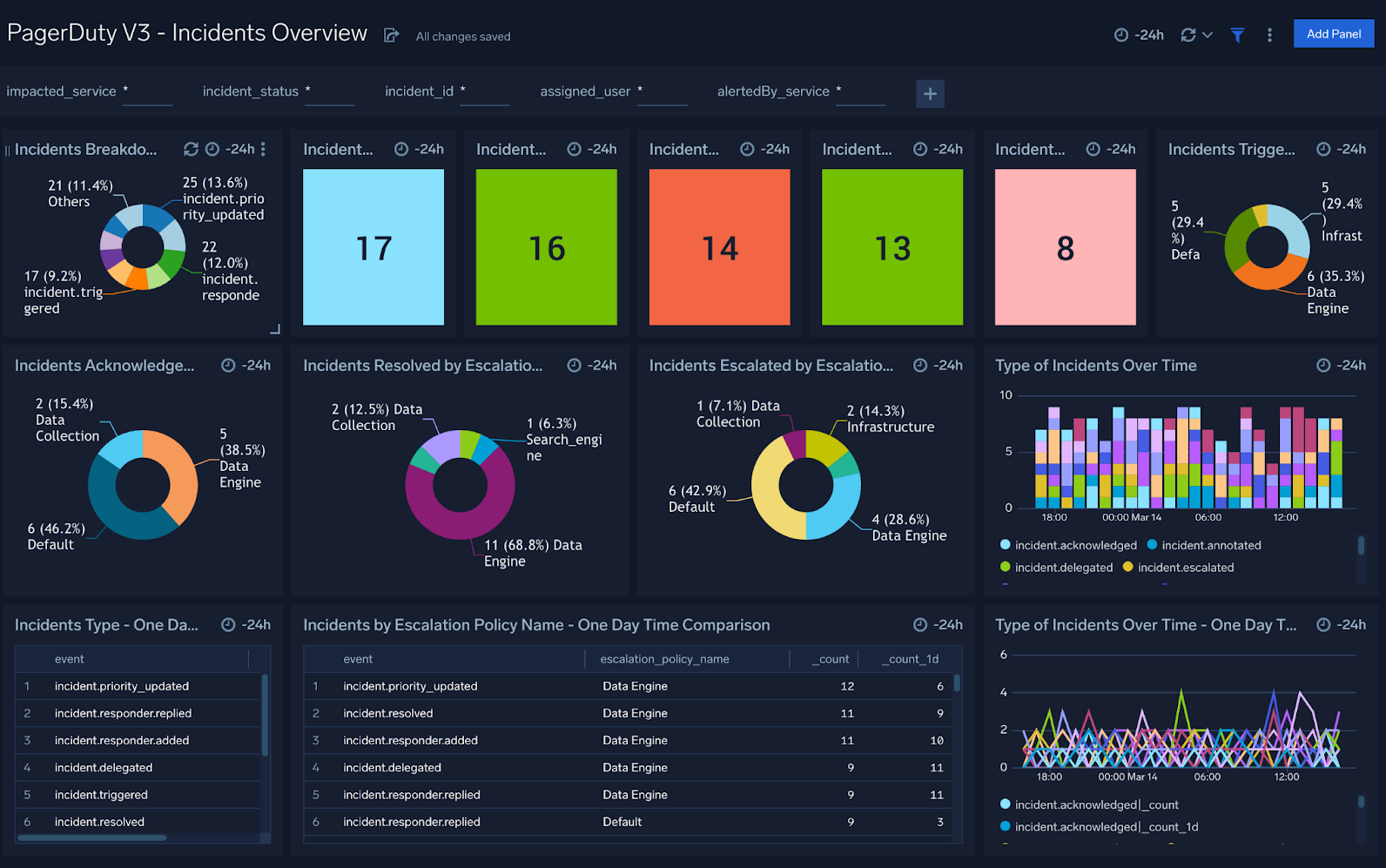
Incidents Overview
PagerDuty V3 - Incidents Overview Dashboard provides an at-a-glance analysis of triggered, acknowledged, escalated, assigned, and resolved incidents. This dashboard also provides a high-level view of incident trends and comparisons over specified time intervals.
Use this dashboard to:
- Review a high-level view of incident summaries.
- Compare the state of incidents with that of a previous time
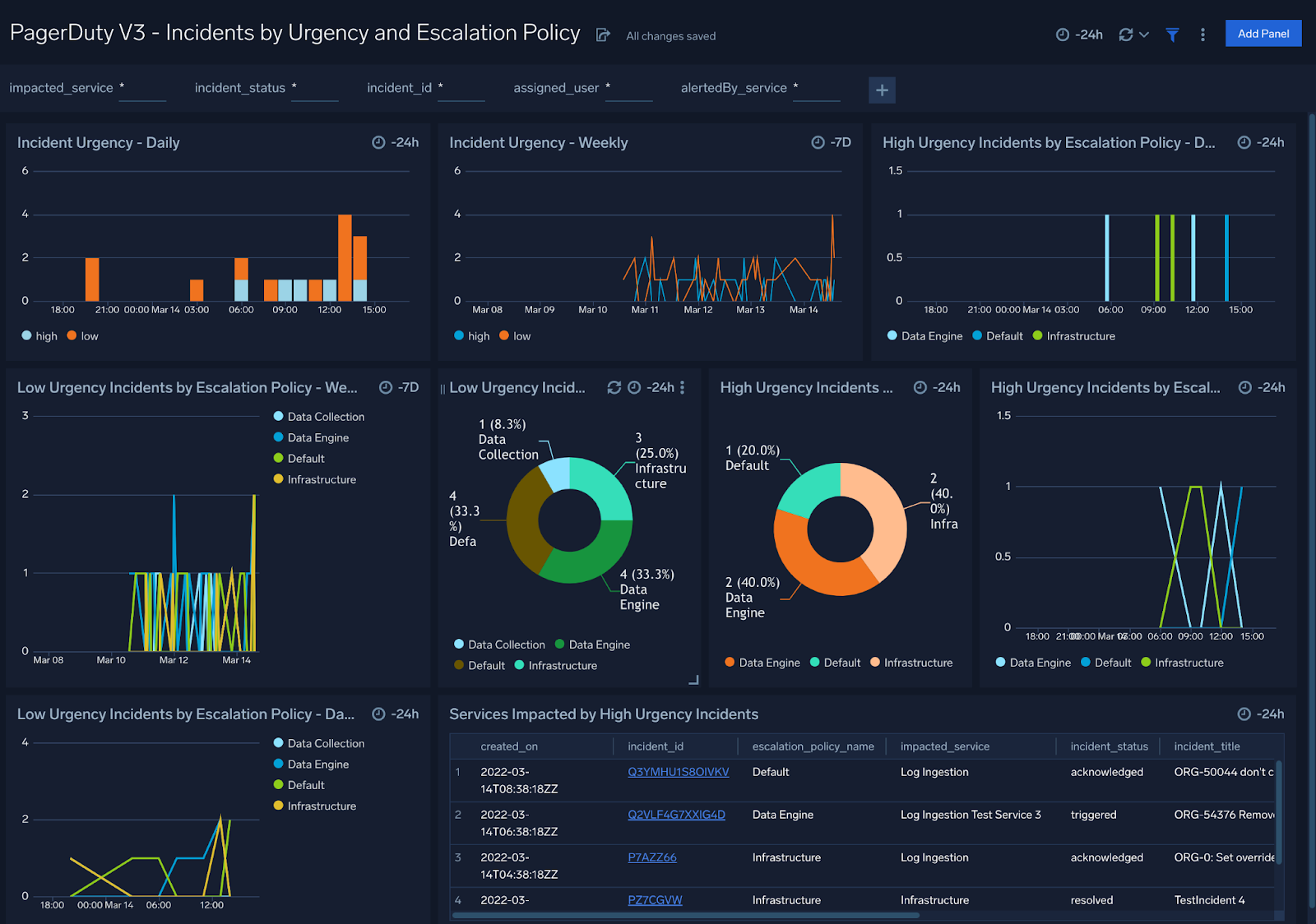
Incidents by Urgency and Escalation Policy
PagerDuty V3 - Incidents by Urgency and Escalation Policy Dashboard provides an overview analysis of urgency events, from low to high, as well as a breakdown of the services impacted by high urgency events.
Use this dashboard to:
- Review see weekly incident summaries.
- Analyze incidents by severity and escalation policy.