Azure AD

Version: 1.10
Updated: Jan 3, 2025
Azure Active Directory (Azure AD) is Microsoft's cloud-based identity and access management service, which helps your employees sign in and access resources.
Actions
- Add Member To Group (Enrichment) - Add a user to a specific group.
- Create Group (Enrichment) - Create a group.
- Create User (Enrichment) - Create a new user.
- Delete Group (Containment) -Delete a specific group.
- Delete User (Containment) - Delete a specific user.
- Disable User (Containment) - Block user account.
- Get Manager (Enrichment) - Get user manager.
- Get Member Groups (Enrichment) - Retrieve a Group memberships for the user.
- Get User (Enrichment) - Get details for a specific user.
- List Devices (Enrichment) - Retrieve a list of device objects registered in the organization.
- List Groups (Enrichment) - List all the groups available in an organization.
- List Of Group Members (Enrichment) - Retrieve a list of members in a specific group.
- List Users (Enrichment) - List all users.
- Remove Member From Group (Containment) - Remove a user from a specific group.
- Reset User Password (Containment) - Reset user password.
- Revoke Sign In Sessions (Containment) - Invalidates all the refresh tokens issued to applications for a user (as well as session cookies in a user's browser).
Azure Active Directory configuration
The following steps show how to create an Azure AD Application in order to work with Sumo Logic automation.
- Log in to Azure portal with the user that has administrator privileges.
- Navigate to Azure Active Directory > App registrations > New registration.
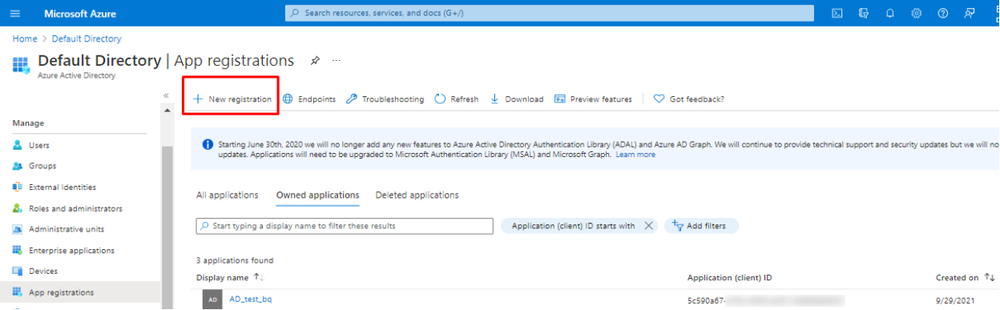
- In the registration form, choose a name for your application and then click Register.
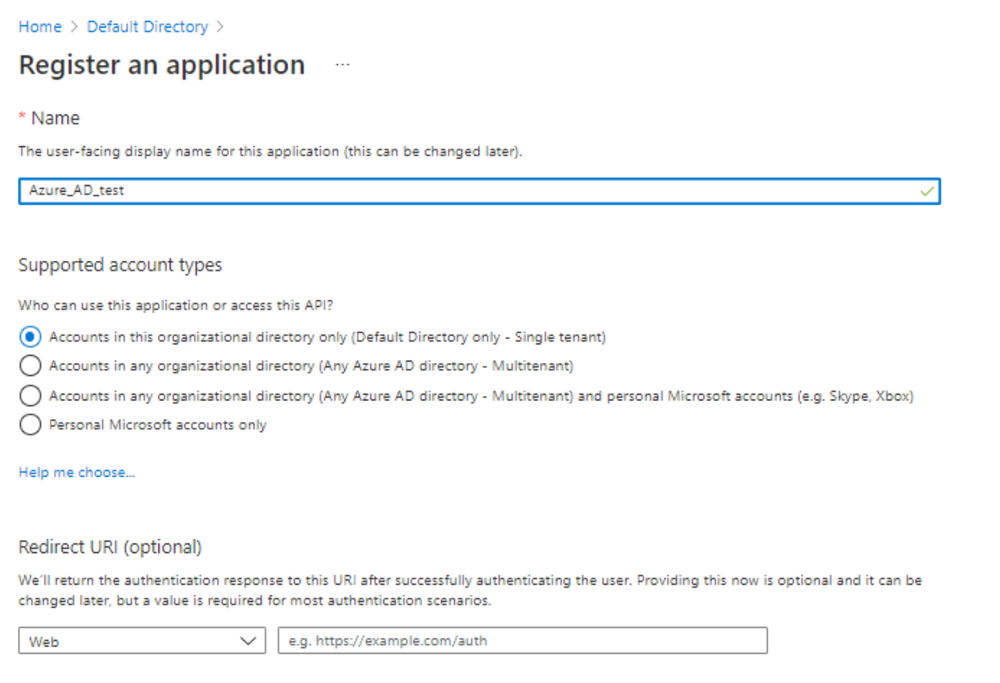
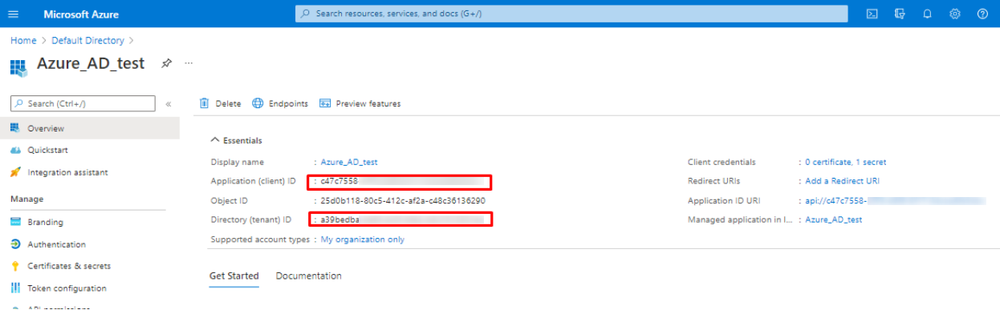
- Write down the Application ID and Directory ID. You will need them later for the integration configuration.
- To configure Azure AD Application permissions, on the left choose API permissions.
- Click the Add a permission button.
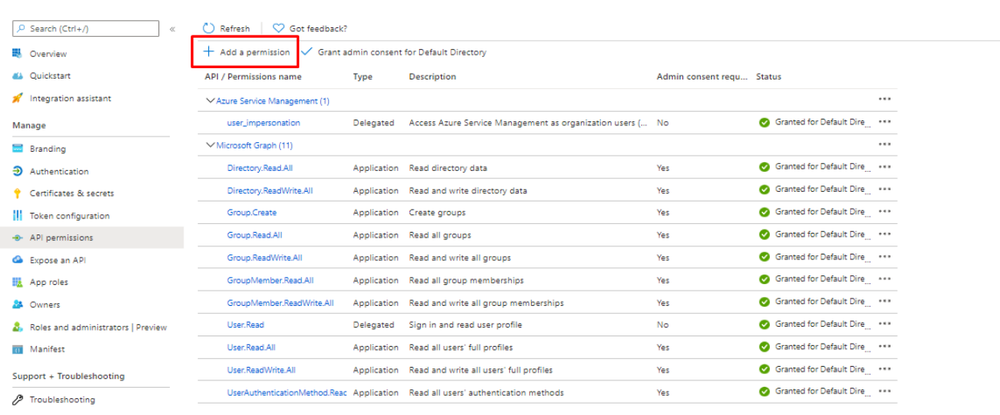
- Select your application in App registrations in the Azure portal.
- Delegated permissions are selected by default.
- Delegated permissions are appropriate for client apps that access an API as the signed-in user, and whose access should be restricted to the permissions you select in the next step.
- Application permissions are for service or daemon-type applications that need to access API as themselves, without user interaction for sign-in or consent.
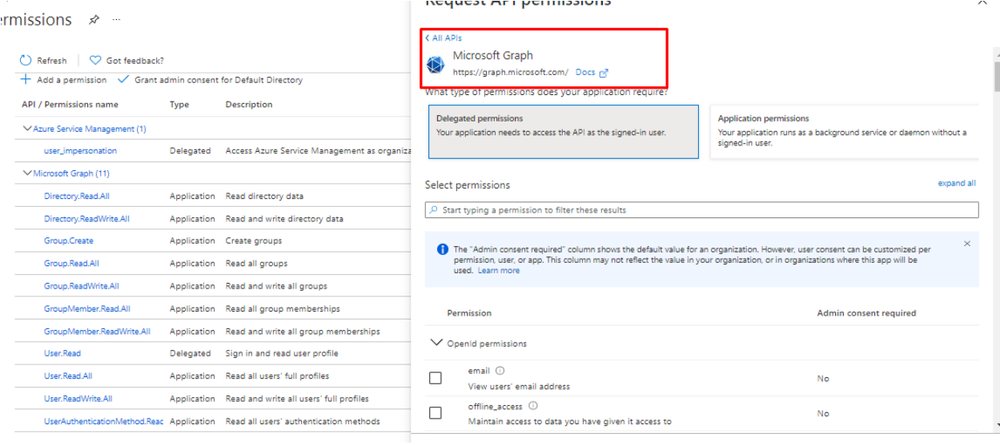
- Select the following permissions to add:
- Delegated (work or school account). User.Read, User.ReadWrite, User.ReadBasic.All, User.Read.All, User.ReadWrite.All, Directory.Read.All, Directory.ReadWrite.All, Directory.AccessAsUser.All.
- Delegated (personal Microsoft account). User.Read, User.ReadWrite.
- Application. User.Read.All, User.ReadWrite.All, Directory.Read.All, Directory.ReadWrite.All.
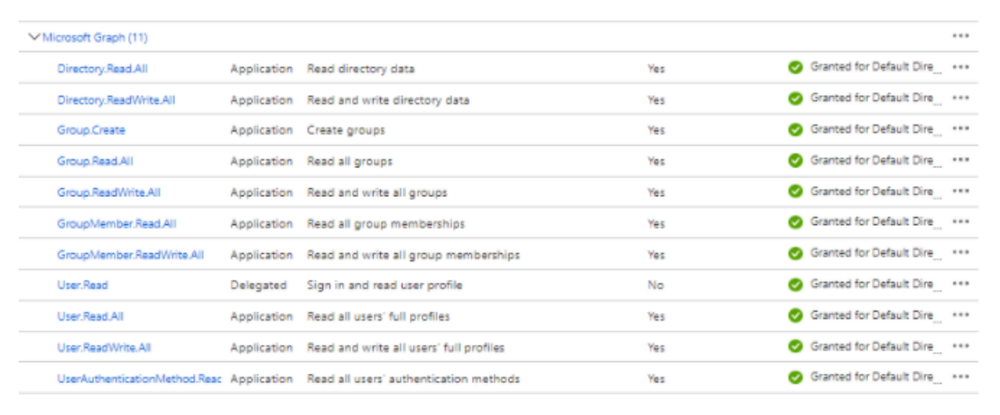
- Once API permission are added then Admin must consent to a grant these permissions (Learn more about permissions and consent.)
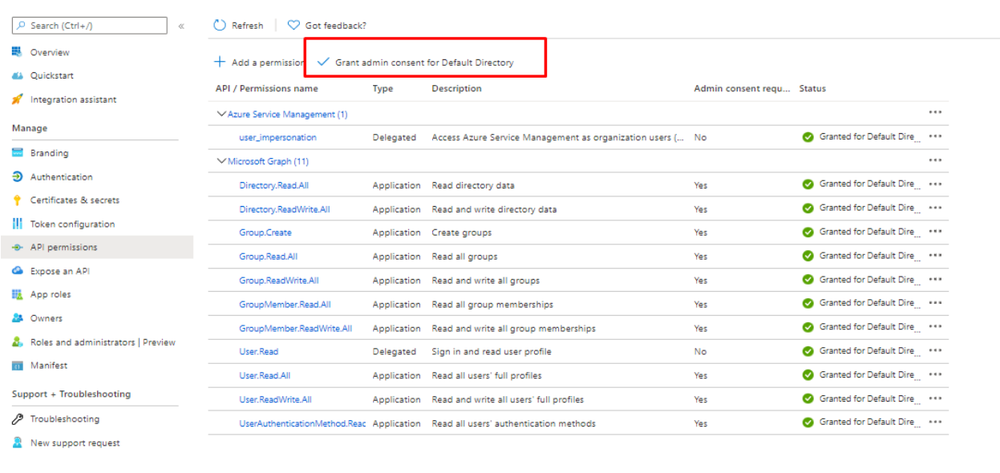
- Once Admin Consent is granted, API permissions configuration have been completed. Then we have to add a Client secret that will be used for the authentication, along with Client ID and Directory ID. To add Client secret, go to Certificates and secrets, and click New client secret.
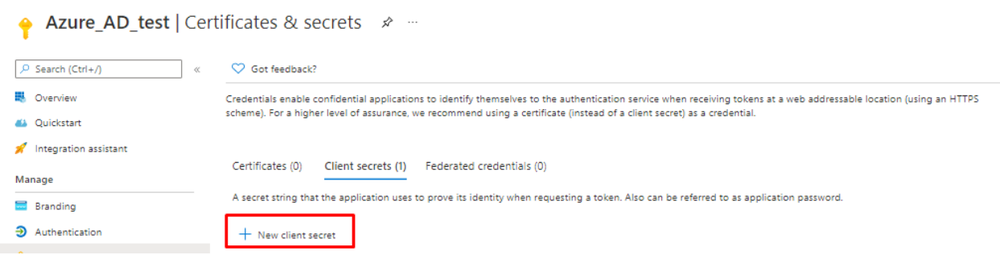
- Select description and expiry period for the created secret and create it.
- Once it's created, make sure you save its value, since its only displayed once.
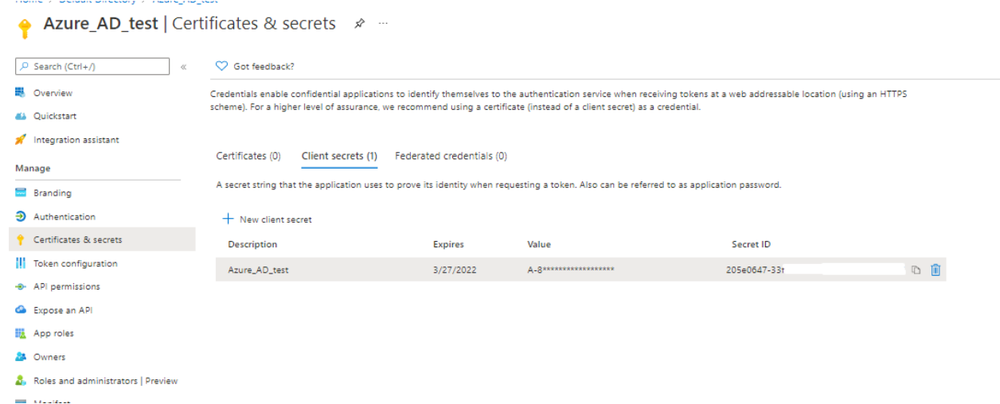
- Once you do these steps you will need to find the Tenant ID in order to use it on your resources file.
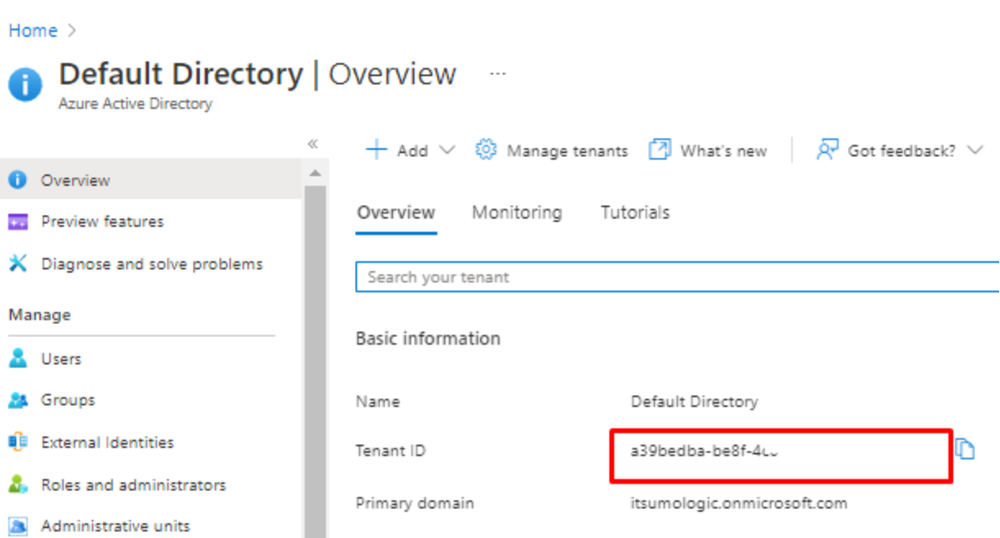
- Configuration of Azure AD application is completed, you will need application’s Client ID, secret, Tenant ID.
- Assign the app the role of User Administrator. This is required to perform action "Reset User Password".
- Azure Active Directory > Roles and administrators > User Administrator > Add assignments > Your app > Add.
Configure Azure AD in Automation Service and Cloud SOAR
Before you can use this automation integration, you must configure its authentication settings so that the product you're integrating with can communicate with Sumo Logic. For general guidance, see Configure Authentication for Automation Integrations.
How to open the integration's configuration dialog
- Access App Central and install the integration. (You can configure at installation, or after installation with the following steps.)
- Go to the Integrations page.
Classic UI. In the main Sumo Logic menu, select Automation and then select Integrations in the left nav bar.
New UI. In the main Sumo Logic menu, select Automation > Integrations. You can also click the Go To... menu at the top of the screen and select Integrations. - Select the installed integration.
- Hover over the resource name and click the Edit button that appears.
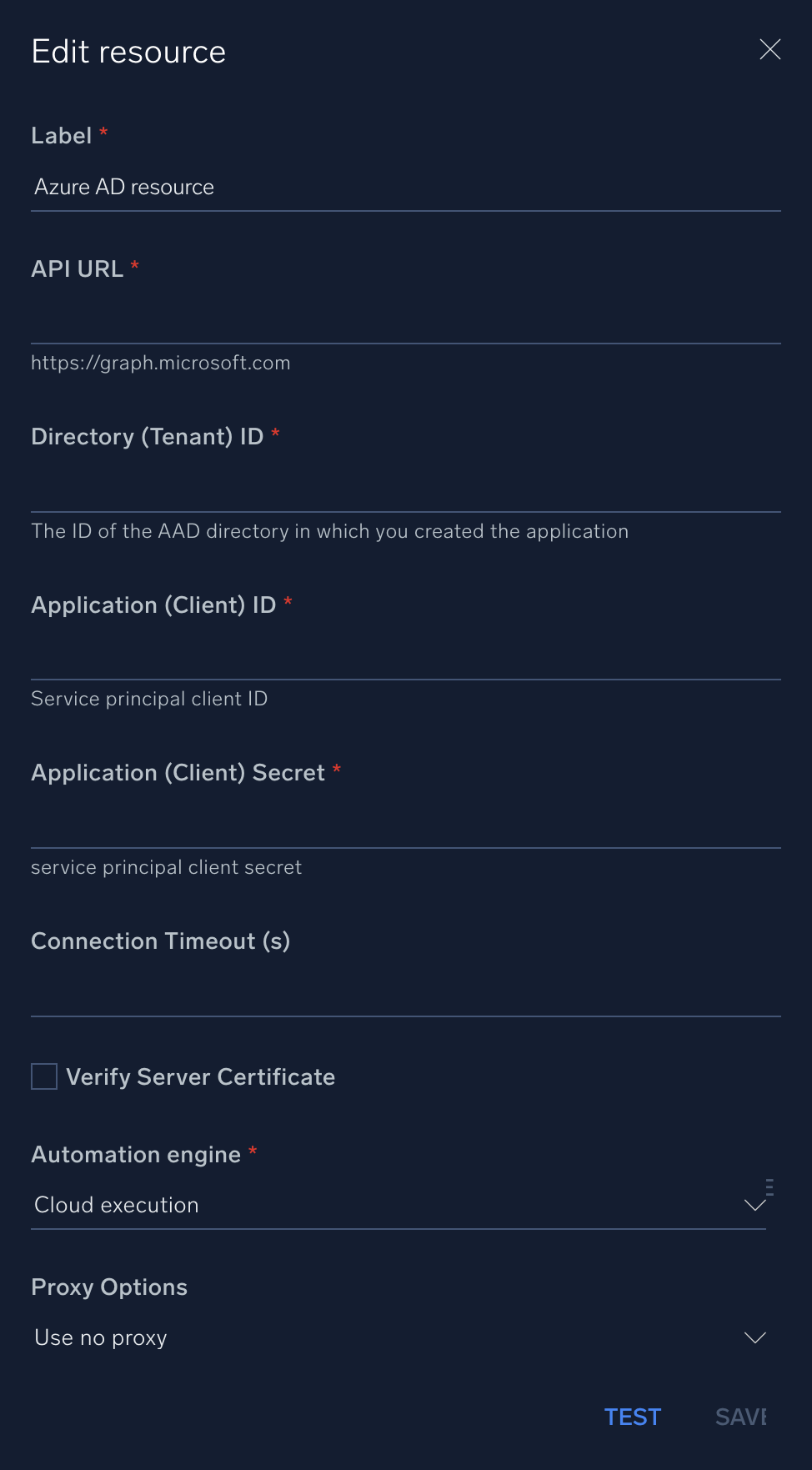
In the configuration dialog, enter information from the product you're integrating with. When done, click TEST to test the configuration, and click SAVE to save the configuration:
-
Label. Enter the name you want to use for the resource.
-
API URL. Enter the Azure AD API URL, for example,
https://graph.microsoft.com -
Directory (Tenant) ID. Enter the tenant ID located when you configured Azure AD above.
-
Application (Client) ID. Enter the client ID from your Azure Application.
-
Application (Client) Secret. Enter your client secret.
-
Connection Timeout (s). Set the maximum amount of time the integration will wait for a server's response before terminating the connection. Enter the connection timeout time in seconds (for example,
180). -
Verify Server Certificate. Select to validate the server’s SSL certificate.
-
Automation Engine. Select Cloud execution for this certified integration. Select a bridge option only for a custom integration. See Cloud or Bridge execution.
-
Proxy Options. Select whether to use a proxy. (Applies only if the automation engine uses a bridge instead of cloud execution.)
- Use no proxy. Communication runs on the bridge and does not use a proxy.
- Use default proxy. Use the default proxy for the bridge set up as described in Using a proxy.
- Use different proxy. Use your own proxy service. Provide the proxy URL and port number.
For information about Microsoft Entra ID (formerly Azure AD), see Entra ID documentation.
Change Log
- October 7, 2021 - First upload
- March 11, 2022 - Logo
- November 10, 2022 (v1.2) - New Action: Get Manager
- April 28, 2023 (v1.3)
- Updated integration: (Updated the integration Fields with Environmental Variables and improved error handling)
- Remove action (Filter Users) as we already have a similar List Users Action
- Changed a few actions type from Containment to Enrichment
- Added New Action List Groups
- June 26, 2023 (v1.4) - Changed multiline hints to single line
- August 25, 2023 (v1.5)
- Added New Action Revoke Sign In Sessions
- August 31, 2023 (v1.6) - Added new actions: List Devices, Disable User
- September 19, 2023 (v1.7) - Versioning
- January 16, 2024 (v1.8)
- Added New Action: Get Member Groups
- November 12, 2024 (v1.9)
- Added New Action: Reset User Password
- January 3, 2025 (v1.10)
- Added New Action:
- List Of Group Members
- Remove Member From Group
- Added New Action: