Cisco Threat Response

Version: 1.2
Updated: Jul 21, 2023
Gather Cisco Threat Response threat intelligence data to enrich incident artifacts.
Actions
- Malware Search (Enrichment) - Search for specific malware strain.
- Sightings Search (Enrichment) - Search for sightings by malware name.
- Vulnerability Search (Enrichment) - Search for vulnerabilities by vulnerability type.
- Enrich Observables (Enrichment) - Gather a verdict for a given cyber observable.
- Extract Observable Type (Enrichment) - Extract Observable Type.
- List Malware (Enrichment) - Get a list of malware signatures.
- List Vulnerabilities (Enrichment) - Get a list of vulnerabilities.
- List Sightings (Enrichment) - Search available sightings.
Configure Cisco Threat Response in Automation Service and Cloud SOAR
Before you can use this automation integration, you must configure its authentication settings so that the product you're integrating with can communicate with Sumo Logic. For general guidance, see Configure Authentication for Automation Integrations.
How to open the integration's configuration dialog
- Access App Central and install the integration. (You can configure at installation, or after installation with the following steps.)
- Go to the Integrations page.
Classic UI. In the main Sumo Logic menu, select Automation and then select Integrations in the left nav bar.
New UI. In the main Sumo Logic menu, select Automation > Integrations. You can also click the Go To... menu at the top of the screen and select Integrations. - Select the installed integration.
- Hover over the resource name and click the Edit button that appears.
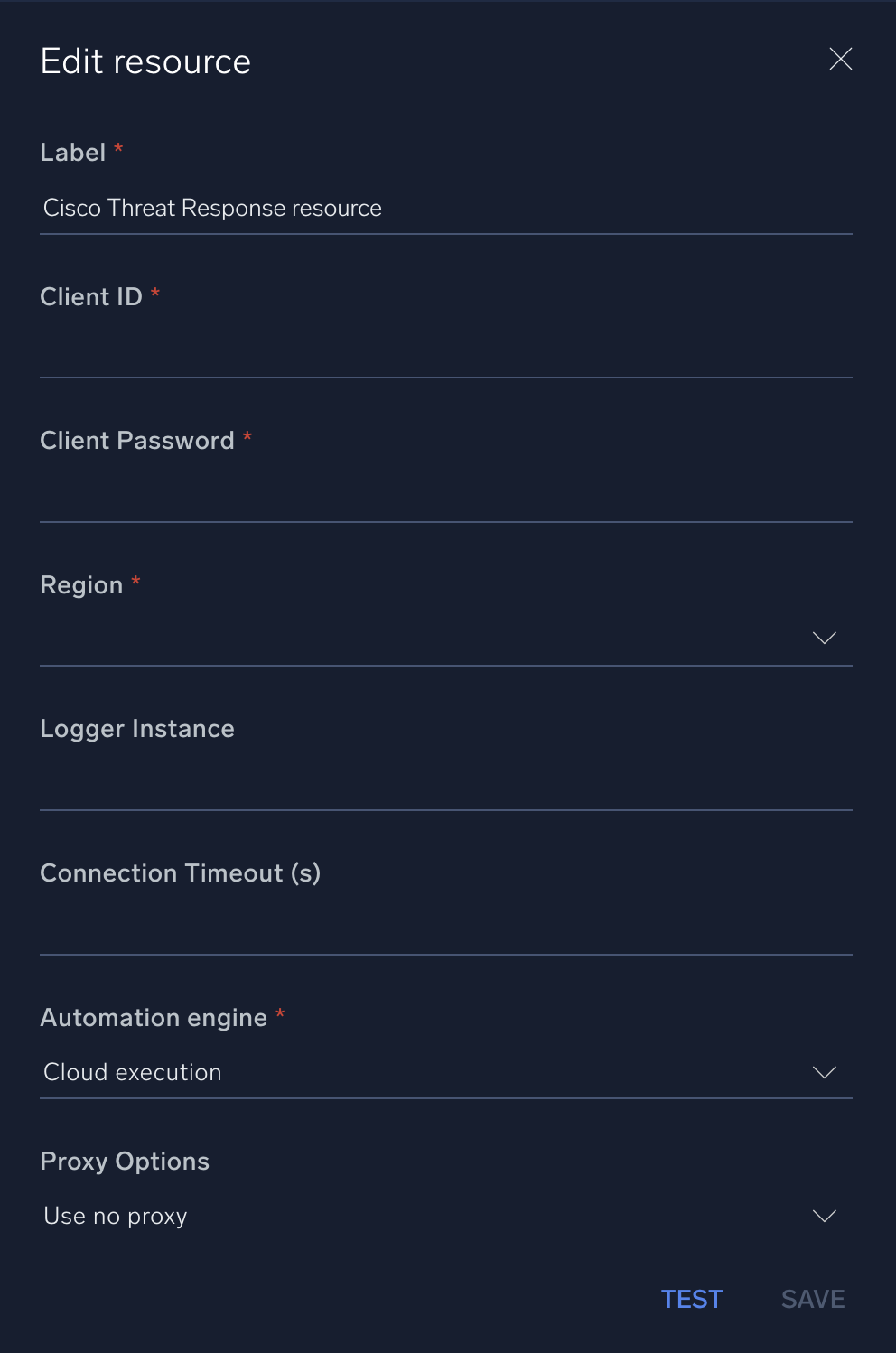
In the configuration dialog, enter information from the product you're integrating with. When done, click TEST to test the configuration, and click SAVE to save the configuration:
-
Label. Enter the name you want to use for the resource.
-
Client ID. Enter a Cisco Threat Response client ID.
-
Client Password. Enter the client password associated with the client ID.
-
Region. Enter the region of your Cisco Threat Response instance.
-
Logger Instance.
-
Connection Timeout (s). Set the maximum amount of time the integration will wait for a server's response before terminating the connection. Enter the connection timeout time in seconds (for example,
180). -
Automation Engine. Select Cloud execution for this certified integration. Select a bridge option only for a custom integration. See Cloud or Bridge execution.
-
Proxy Options. Select whether to use a proxy. (Applies only if the automation engine uses a bridge instead of cloud execution.)
- Use no proxy. Communication runs on the bridge and does not use a proxy.
- Use default proxy. Use the default proxy for the bridge set up as described in Using a proxy.
- Use different proxy. Use your own proxy service. Provide the proxy URL and port number.
For information about Cisco Threat Response, see Cisco Threat Response documentation.
Change Log
- February 21, 2020 - First upload
- May 22, 2020 - New actions added
- July 21, 2023 (v1.2) - Integration refactored