VMware Carbon Black Cloud Platform

Version: 2.4
Updated: Mar 4, 2024
VMware Carbon Black Cloud Platform Integration transform your security with intelligent endpoint and workload protection that adapts to your needs, allows security operators to collect CBC Alerts and Devices information and take action on remote endpoints to Quarantine it or update the Policy of endpoints.
Actions
- Carbon Black Alerts Daemon (Daemon) - Automatically gather alerts from Carbon Black Cloud.
- Add Alert Note (Notification) - Add a note to an alert.
- Delete Endpoint File (Containment) - Delete a File from a device.
- Disable Bypass (Containment) - Disable Bypass on specific Endpoint.
- Dismiss Alert (Containment) - Dismiss an alert in Carbon Black Cloud with comments.
- Dismiss Threat (Containment) - Dismiss a Threat in Carbon Black Cloud with comments.
- Enable Bypass (Containment) - Enable Bypass on specific Endpoint, it should no longer be monitored but may need to in the future.
- Execute Custom Script On Endpoint (Containment) - Execute a PowerShell command on a windows endpoint to gather data.
- Get CBC Alerts (Enrichment) - Queries all Alerts using input search criteria and returns a list of alerts.
- Get Devices (Enrichment) - Retrieve info about a device.
- Get Endpoint Vulnerabilities (Enrichment) - Get the vulnerabilities (CVEs) and their risks/exploitability identified for a given endpoint.
- Get File (Enrichment) - Get the full contents of a suspicious MS Office or PowerShell file that is executed on an endpoint.
- Get Policies (Enrichment) - Get a list of Policies.
- Get Process Details (Enrichment) - Get the most up-to-date metadata of a specific process.
- Get Process Events (Enrichment) - Get relevant endpoint events of a watchlist hit. This is very resource-intensive for CBC and should be used sparingly.
- Get Registry Key (Enrichment) - Identify if a specific registry key has been set.
- Get Vulnerable Endpoints (Enrichment) - Given a vulnerability (CVE) identify which endpoints are vulnerable.
- Kill Process By Path (Containment) - Kill a malicious process by path if it’s still running.
- Kill Process By PID (Containment) - Kill a malicious process by PID if it’s still running.
- List Endpoint Directory (Enrichment) - List the files, including metadata such as size and last write time directly from the endpoint.
- List Running Processes (Enrichment) - Identify if the malicious process is still running.
- Pause Background Scan (Containment) - If the endpoint is sensitive to high CPU, disable background scanning.
- Quarantine Device (Containment) - When the endpoint is suspected to be compromised, isolate it so that the only network communication allowed is with Carbon Black Cloud.
- Search Process (Enrichment) - Find all endpoints where a certain process (by name or hash) has been executed. Find all processes by reputation.
- Start Background Scan (Containment) - Start Background Scan on an endpoint.
- Unquarantine Device (Containment) - Remove the quarantine on the specified Device within Carbon Black.
- Update Device Policy (Containment) - Move the endpoint to a more restrictive policy.
VMware Carbon Black Cloud Platform configuration
- Log in to the CBC Console.
- Navigate to the Settings menu, and then click on API Access.
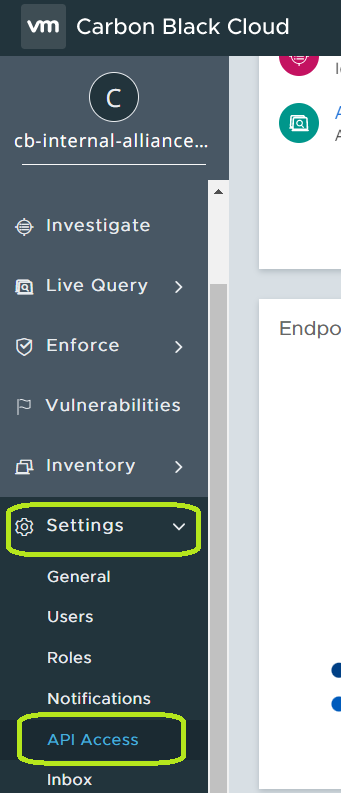
- From the API ACCESS page, click on Add API Key.
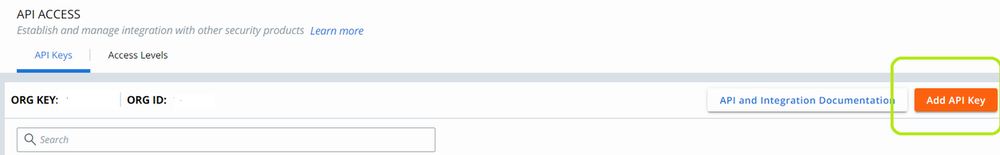
- Populate the name, Access Level type, and click the Save button.
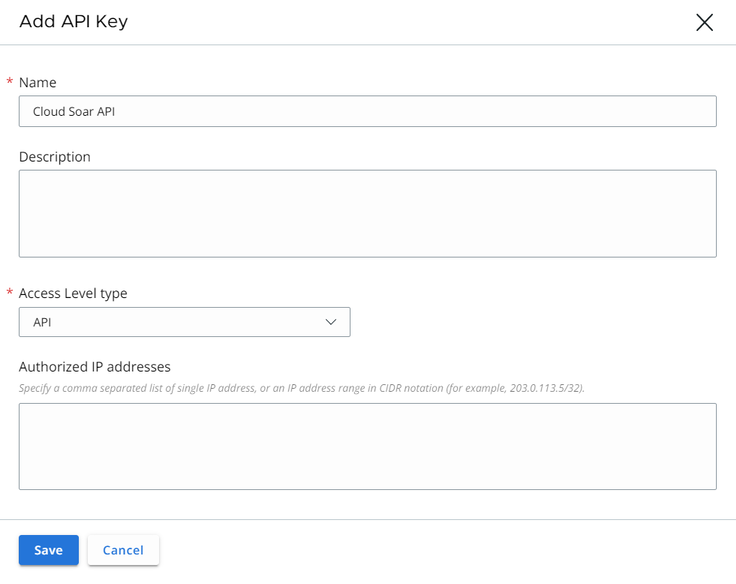
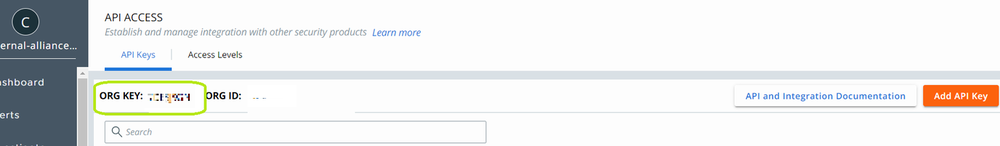
- Copy the API Credentials (API ID and API Secret Key).

- Also you will see the ORG KEY from API Access. You need to copy it.
Configure VMware Carbon Black Cloud Platform in Automation Service and Cloud SOAR
Before you can use this automation integration, you must configure its authentication settings so that the product you're integrating with can communicate with Sumo Logic. For general guidance, see Configure Authentication for Automation Integrations.
How to open the integration's configuration dialog
- Access App Central and install the integration. (You can configure at installation, or after installation with the following steps.)
- Go to the Integrations page.
Classic UI. In the main Sumo Logic menu, select Automation and then select Integrations in the left nav bar.
New UI. In the main Sumo Logic menu, select Automation > Integrations. You can also click the Go To... menu at the top of the screen and select Integrations. - Select the installed integration.
- Hover over the resource name and click the Edit button that appears.
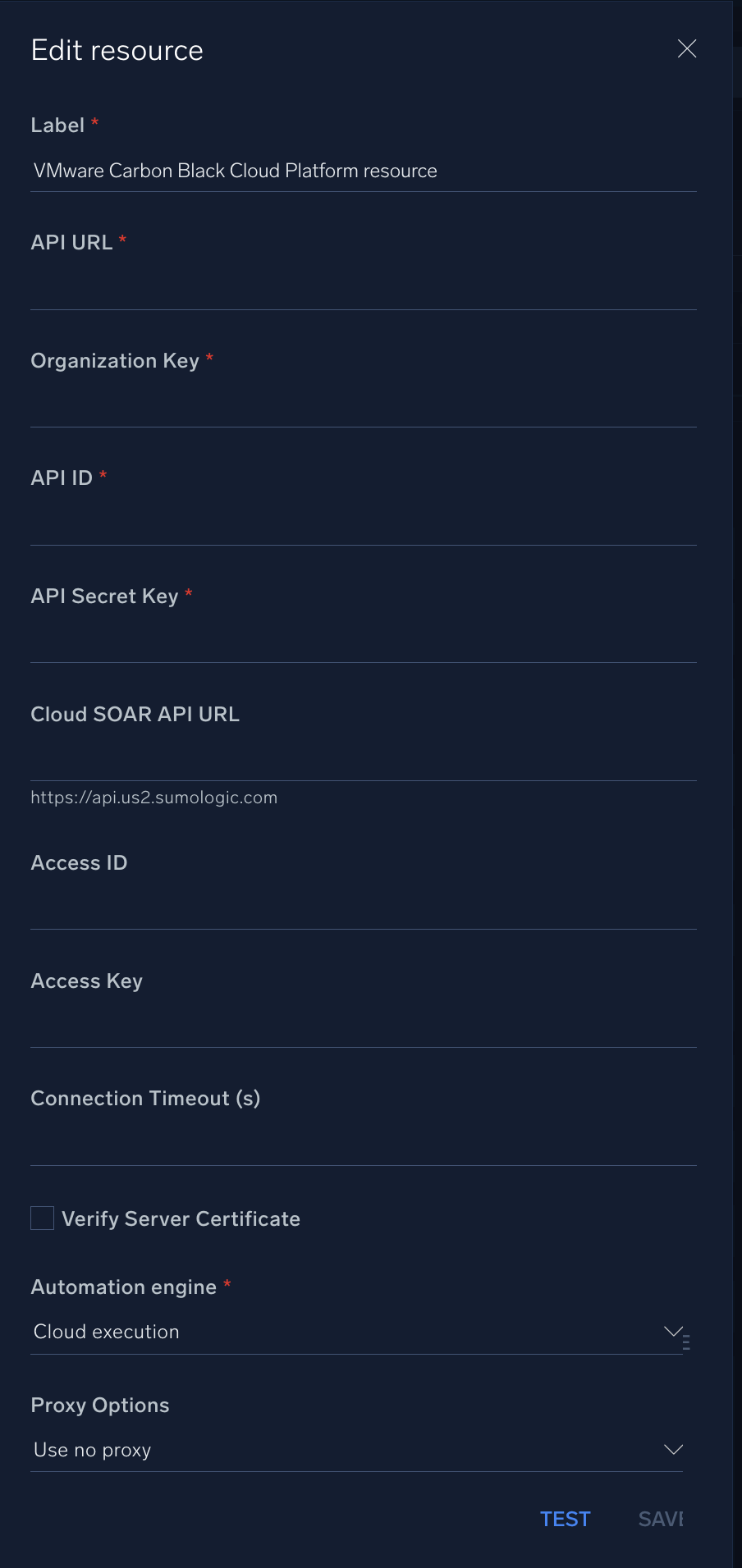
In the configuration dialog, enter information from the product you're integrating with. When done, click TEST to test the configuration, and click SAVE to save the configuration:
-
Label. Enter the name you want to use for the resource.
-
API URL. URL to the API of the VMware Carbon Black Cloud Platform instance
https://defense.conferdeploy.net. -
Organization Key. The organization key you copied earlier.
-
API ID / Connector ID. The API ID that you copied earlier.
-
API Secret Key. The secret for the API ID that you copied earlier.
-
Cloud SOAR API URL. Enter your Sumo Logic API URL (for example,
https://api.us2.sumologic.com). Enter the API endpoint URL for your region. -
Access ID. Enter the access ID for your Sumo Logic access key. Select Default as the scope when generating access keys.
-
Access Key. Enter the access key corresponding to your Sumo Logic access ID.
-
Connection Timeout (s). Set the maximum amount of time the integration will wait for a server's response before terminating the connection. Enter the connection timeout time in seconds (for example,
180). -
Verify Server Certificate. Select to validate the server’s SSL certificate.
-
Automation Engine. Select Cloud execution for this certified integration. Select a bridge option only for a custom integration. See Cloud or Bridge execution.
-
Proxy Options. Select whether to use a proxy. (Applies only if the automation engine uses a bridge instead of cloud execution.)
- Use no proxy. Communication runs on the bridge and does not use a proxy.
- Use default proxy. Use the default proxy for the bridge set up as described in Using a proxy.
- Use different proxy. Use your own proxy service. Provide the proxy URL and port number.
For information about Carbon Black Cloud, see Carbon Black Cloud documentation.
External Libraries
Category
EDR
Change Log
- April 7, 2022 - First upload
- May 11, 2022 - Refactored all actions with CBC SDK
- June 08, 2022 - Updated integration doc
- July 19, 2023 (v2.2) - Removed leading/trailing spaces
- November 7, 2023 (v2.3) - Updated integration for compatibility with new Cloud SOAR API
- March 4, 2024 (v2.4) - Updated code for compatibility with Python 3.12