Configure Authentication for Automation Integrations
This article provides a quick reference to configure authentication for automation integrations in App Central for the Automation Service and Cloud SOAR. Refer to the individual integrations articles for detailed information on setup, usage, and features.
How to configure authentication for automation integrations
- Access App Central and install the integration from App Central.
- Select the installed integration in the Integrations page.
New UI. In the main Sumo Logic menu, select Automation > Integrations. You can also click the Go To... menu at the top of the screen and select Integrations.
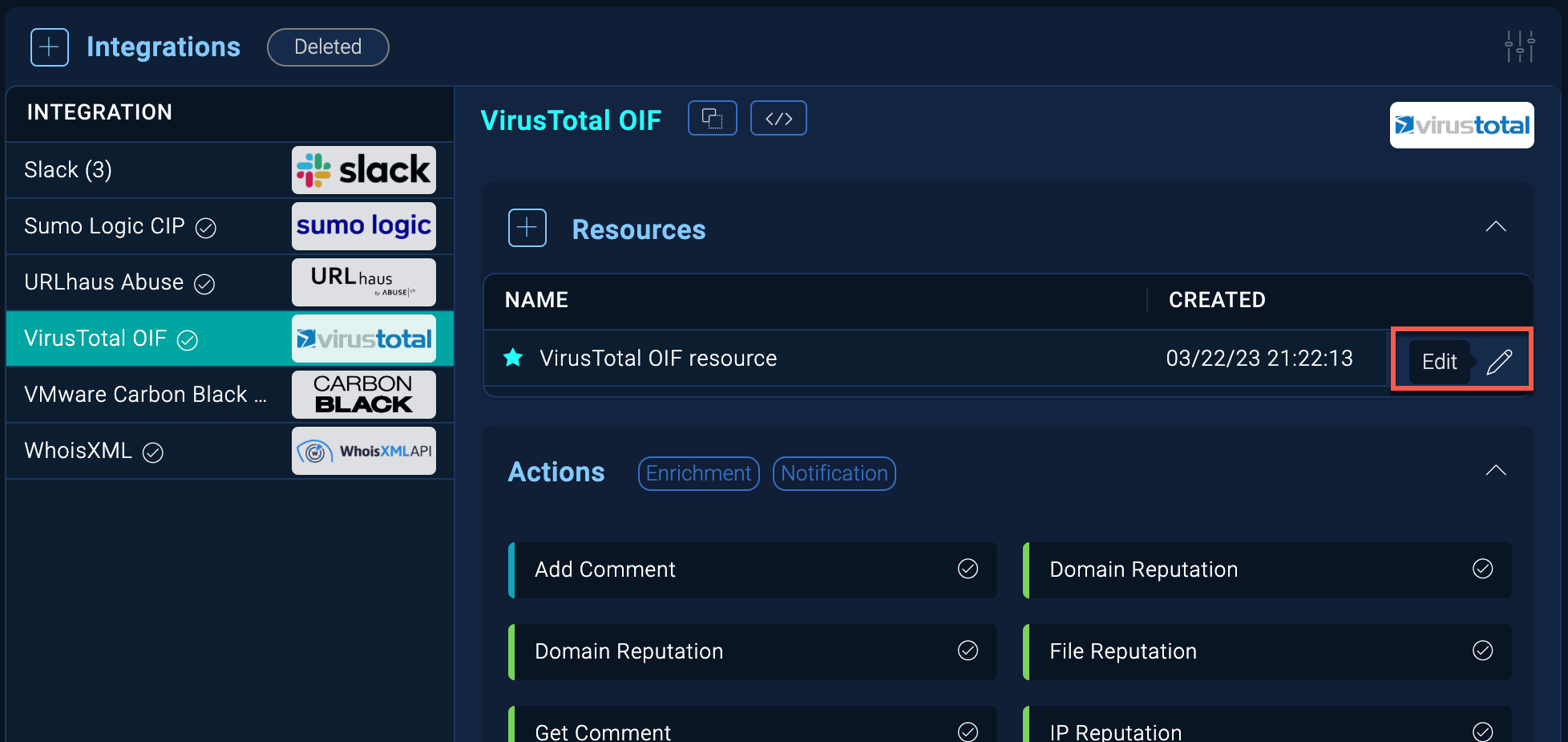
Classic UI. In the main Sumo Logic menu, select Automation and then select Integrations in the left nav bar. - Select the integration whose resource you want to configure the connection for.
- Hover over the resource name and click the Edit button that appears.
- Enter the authentication needed by the resource.
What you enter is specific to the resource you're using. Each resource's configuration screen may be different, but in most cases, you will need information such as IP addresses, API tokens, usernames, and passwords for the application you're integrating with.
For example, in the following screen enter the API URL and API Key from the vendor.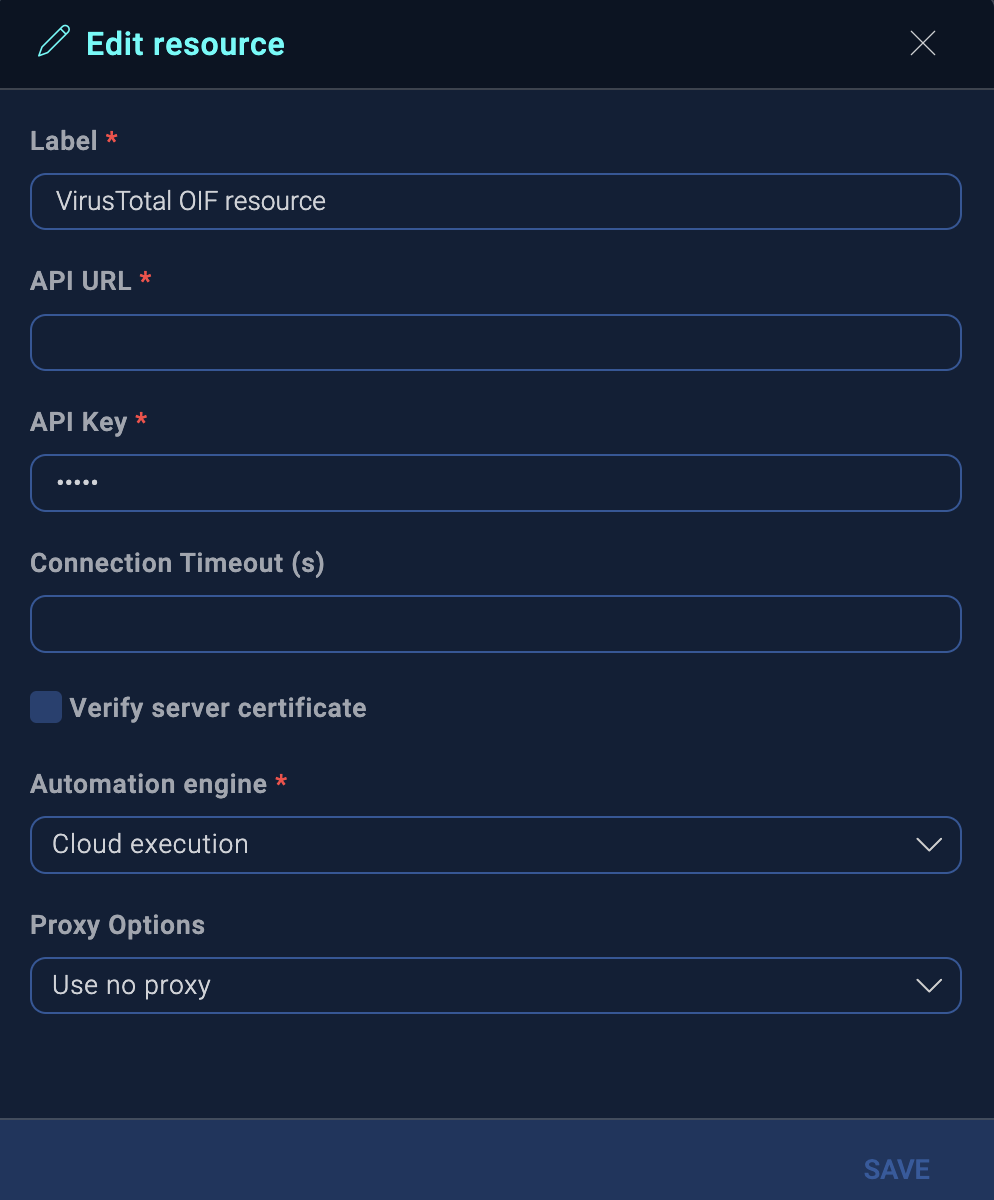 note
noteIn many integrations, the configuration screen asks you to do the following:
- Provide the Sumo Logic API URL (for example,
https://api.sumologic.com). Enter the API endpoint URL for your region. - Enter the Access ID and Access Key from a Sumo Logic access key. Select Default as the scope when generating access keys.
- Provide the Sumo Logic API URL (for example,
- When done, click TEST to test the configuration.
- Click SAVE to save the configuration.
Authentication needed for automation integrations
Authentication for common integrations
The following outlines the authentication requirements for commonly used integrations:
- HTTP Tools:
- For HTTP API URL provide the resource-specific URL.
- In Extra Headers add required auth tokens (if applicable) as JSON input or key-value pairs. Verify that the auth token provided has the necessary permissions for the requested playbook actions.
- Incident Tools / Mail Tools / Triage Tools / Zip Tools:
- Set the Cloud SOAR API URL (for example,
https://api.sumologic.com). Enter the API endpoint URL for your region. - Provide the Access ID and Access Key from a Sumo Logic access key. Select Default as the scope when generating access keys.
- Set the Cloud SOAR API URL (for example,
- Sumo Logic Cloud SIEM:
- Provide the Sumo Logic API URL (for example,
https://api.sumologic.com). Enter the API endpoint URL for your region. - Enter the Access ID and Access Key from a Sumo Logic access key. Select Default as the scope when generating access keys.
- Provide the Sumo Logic API URL (for example,
- Sumo Logic Log Analytics:
- Provide the Sumo Logic API URL (for example,
https://api.sumologic.com). Enter the API endpoint URL for your region. - Enter the Access ID and Access Key from a Sumo Logic access key. For minimal configuration, select the scope Log Search or other relevant scopes as required.
- Provide the Sumo Logic API URL (for example,
- Sumo Logic Notifications:
- Provide the Sumo Logic API URL (for example,
https://api.sumologic.com). Enter the API endpoint URL for your region. - Enter the Access ID and Access Key from a Sumo Logic access key. Select Default as the scope when generating access keys.
- Provide the Slack Bot/User OAuth Token.
- Provide the Sumo Logic API URL (for example,
- Sumo Logic Notifications by Gmail:
- Provide the Sumo Logic API URL (for example,
https://api.sumologic.com). Enter the API endpoint URL for your region. - Enter the Access ID and Access Key from a Sumo Logic access key. Select Default as the scope when generating access keys.
- Provide Client ID (Gmail) and Client Secret ID (Gmail) setup steps obtained as described here.
- Configure authorization separately from the playbook (initial one-time setup).
- Provide the Sumo Logic API URL (for example,
- Sumo Logic Notifications by Microsoft:
- For the first API URL field, provide the Microsoft Graph API URL.
- Specify the Authentication Grant Type and Directory (Tenant) ID.
- For Client ID and Client Secret, provide the Microsoft Graph client ID and secret obtained as described in Add a client secret.
- Provide the Sumo Logic API URL (for example,
https://api.sumologic.com). Enter the API endpoint URL for your region. - Enter the Access ID and Access Key from a Sumo Logic access key. Select Default as the scope when generating access keys.
Integrations not requiring authentication
These integrations execute without additional authentication:
- Basic Tools
- Sumo Logic Automation Tools
- Sumo Logic Cloud SIEM Internal
- Sumo Logic Log Analytics Internal
Troubleshooting general issues
Sumo Logic access key doesn't work
To resolve access key issues:
- Confirm the Access ID and Access Key are correctly copied from the Access Keys page.
- Ensure your key has the Default scope and hasn't expired.
- Ensure permissions tied to your access key allow the specific integration actions being attempted.
- If issues persist, regenerate your access key and retry.
API endpoint and error issues
To resolve Sumo Logic API endpoint errors, verify the API endpoint URL matches your deployment region (for example, us1, us2, eu).
To resolve vendor API endpoint errors:
- Validate integration setup via the third-party vendor’s dashboard or Postman.
- Configure API tokens and access keys with the appropriate scope.
- Check if authentication credentials and API parameters are correct.
- Review the vendor’s API documentation:
- Identify the correct authentication method.
- Define minimum permissions required.
- Validate endpoint URLs and API parameters.
Examples of vendor API documentation:
For additional help with APIs, contact support.
Permissions issues
Where possible, permissions should be granted in accordance with the principle of least privilege.
Permissions depend on the integration’s use case. Users should:
- Refer to the vendor API documentation for required credentials.
- Configure API tokens and access keys with the appropriate scope.
Vendor site is not available
Use Check-Host to monitor website and host availability and performance.
Troubleshooting vendor-specific issues
AWS integrations
This section applies to all AWS integrations, (for example, AWS EC2, AWS S3, etc.)
For AWS service endpoints information, see AWS documentation.
Authentication method
AWS recommends using IAM roles with temporary security credentials over long-term access keys for enhanced security.
To enable AWS IAM role-based authentication without sharing access keys and secrets, follow the steps below:
- Create an IAM role in your AWS account. Follow AWS’s guide to create a new IAM role.
- Attach required policies to the role depending on the AWS services you want to allow access to (for example,
AmazonEC2ReadOnlyAccess,AWSWAFFullAccess, etc.). - Update the trust policy to allow Sumo Logic’s AWS account to assume this role. This involves editing the trust relationship JSON to include Sumo Logic’s AWS account ID as a trusted principal.
Example trust policy:
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Principal": {
"AWS": "arn:aws:iam::926226587429:root"
},
"Action": "sts:AssumeRole"
}
]
}
Regional configuration
A single integration can be used across multiple AWS regions. However, if region-specific actions are required in playbooks, separate resources must be created, and conditional logic can be applied for selection.
Service specifics
- Service name. Use the name of the specific AWS service (for example, S3, EC2).
- Host/URL. Must be service-specific and regional (for example,
s3.amazonaws.com). - Session token. Required for temporary authentication.
- Scope. Defines access permissions based on IAM policies.
CyberArk
For CyberArk PAM, obtain client certificates, private keys, and root CA certificates via CyberArk Docs.
Slack
For the Slack and Sumo Logic Notifications integrations, a Slack OAuth token is required because the integration specifically sends notifications from Sumo Logic to Slack channels.
Sumo Logic Log Analytics
Users often ask what is the difference between the Sumo Logic Log Analytics Internal and Sumo Logic Log Analytics integrations.
Sumo Logic Log Analytics Internal is designed for internal actions. It requires no additional authentication as it's integrated directly within the Sumo Logic environment. It is used primarily for simple automation within the platform without external API calls.
Sumo Logic Log Analytics requires API-based authentication (Access ID and Access Key) and is intended for external API calls or extended functionality beyond internal tools.