About Sumo Logic Threat Intelligence
Threat intelligence, often abbreviated as threat intel, is information that helps you prevent or mitigate cyber attacks. Threat intelligence indicators are individual data points about threats that are gathered from external sources about various entities such as host names, file hashes, IP addresses, and other known possible sources of attack and compromise.
Threat intelligence indicators can help security analysts leverage a large body of information to surface potential threats. For example, say that a threat intelligence database has an indicator that correlates a certain IP address with known malicious activity. Because of this correlation, analysts can assume log messages with that IP address are more likely to be part of a real cyber attack.
Cybersecurity professionals often use multiple threat intelligence feeds to supply them with indicators. Having a wide net allows them to catch more threats. See our blog Threat intelligence feeds: essential arsenal in cybersecurity.
Threat intelligence sources
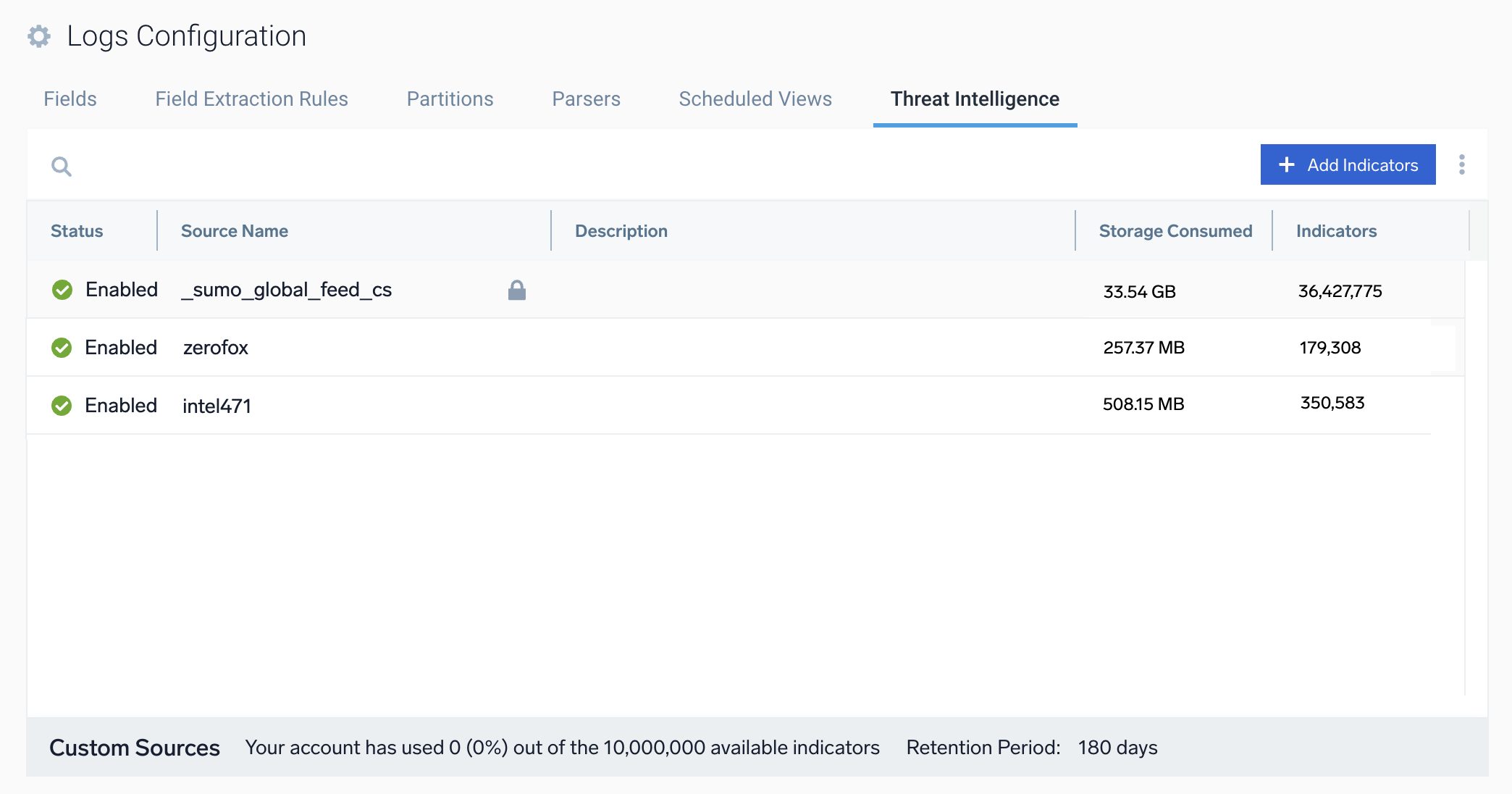
In Sumo Logic, threat intelligence indicators are supplied by sources listed on the Threat Intelligence tab.
- New UI. To access the Threat Intelligence tab, in the main Sumo Logic menu select Data Management, and then under Logs select Threat Intelligence. You can also click the Go To... menu at the top of the screen and select Threat Intelligence.
- Classic UI. To access the Threat Intelligence tab, in the main Sumo Logic menu, select Manage Data > Logs > Threat Intelligence.
Cloud SIEM analysts can use all sources shown in the Threat Intelligence tab to find threats (see Find Threats with Cloud SIEM). In addition, all Sumo Logic users can run queries against the indicators in the Sumo Logic threat intelligence sources to uncover threats (see Find Threats with Log Queries).
Only Cloud SIEM administrators can add threat intelligence indicators to the datastore.
The sources on the Threat Intelligence tab include:
- Sumo Logic sources. Out-of-the-box default sources of threat indicators supplied by third party intel vendors and maintained by Sumo Logic. You cannot edit these sources. See Sumo Logic threat intelligence sources below.
- Other sources. The other sources on the tab are imported by Cloud SIEM administrators so that Cloud SIEM analysts can use them to find threats. See Ingest threat intelligence indicators to learn how to add other sources.
Sumo Logic threat intelligence sources
Sumo Logic provides the following out-of-the-box default sources of threat indicators supplied by third party intel vendors and maintained by Sumo Logic. You cannot edit these sources:
- SumoLogic_ThreatIntel. This source incorporates threat indicators supplied by Intel 471.
- _sumo_global_feed_cs. This is a source of threat indicators supplied by CrowdStrike.
Ingest threat intelligence indicators
A Cloud SIEM administrator must first ingest the indicators before they can be used to uncover threats. Indicators can be ingested using:
- A collector. See:
- The API. See the following APIs in the Threat Intel Ingest Management API resource:
- The Threat Intelligence tab. Use this tab to upload your own indicators. See Add indicators in the Threat Intelligence tab. See Upload formats for the format to use when uploading indicators using this tab or APIs.
After threat indicator sources are ingested, they appear on the Threat Intelligence tab and are ready to be used in Cloud SIEM rules.
Only Cloud SIEM administrators can add threat intelligence indicators to the datastore.
- Sumo Logic's threat intelligence data store only ingests simple threat indicators, not complex indicators that outline a series of steps or entities that make up an attack. Nor does it ingest actors, malware, or other object types.
- The limit of the number of indicators that can be uploaded in one API call is 100.
- When you add indicators, the event is recorded in the Audit Event Index. See Audit logging for threat intelligence.
Prerequisites
Role capabilities
To view and manage threat intelligence indicators on the Threat Intelligence tab, a Cloud SIEM administrator must have the correct role capabilities.
- New UI. In the main Sumo Logic menu select Administration, and then under Users and Roles select Roles. You can also click the Go To... menu at the top of the screen and select Roles.
Classic UI. In the main Sumo Logic menu, select Administration > Users and Roles. - Click the Roles tab.
- Click Add Role to create a new role. Alternatively, you can select an existing role in the Roles tab and click Edit.
Add the following capabilities:
- Threat Intel
- View Threat Intel Data Store
- Manage Threat Intel Data Store
- Threat Intel
You do not need to be assigned these role capabilities to find threats with log queries.
Typical workflow
Here is the typical workflow to set up and use threat intelligence indicators:
- A system administrator ingests threat intelligence indicators and adds them to the threat intelligence data store. For example, install a collector such as the STIX/TAXII 2 Client Source, and set up the collector to obtain indicators from Federal, vendor, or open services. Ingested indicators appear on the Threat Intelligence tab. You can manually add more indicators as needed, such as your own private indicators, using the Threat Intelligence tab or the Threat Intel Ingest Management APIs.
- Analysts use the threat indicators data to uncover threats using Cloud SIEM rules.
- A system administrator occasionally checks to see why a connector isn’t ingesting data, or to see how much storage all the indicators are using. They may examine their indicators, and then if needed, delete indicators.
Audit logging for threat intelligence
Use the Audit Event Index to view events for threat indicators, such as adding indicators, removing indicators, or changing the retention period.
Use a search like the following:
_index=sumologic_audit_events _sourceCategory=threatIntelligence