Manage Threat Intelligence Indicators
The Threat Intelligence tab shows the indicators that have been added to your threat intelligence datastore. Use this tab to add and manage your threat intelligence indicators. You can add indicators from a number of sources (see Ingest threat intelligence indicators). Threat intelligence indicators imported to Sumo Logic not only integrate with your existing core Sumo Logic deployment, but also Cloud SIEM and Cloud SOAR.
Threat Intelligence tab
New UI. To access the Threat Intelligence tab, in the main Sumo Logic menu select Data Management, and then under Logs select Threat Intelligence. You can also click the Go To... menu at the top of the screen and select Threat Intelligence.
Classic UI. To access the Threat Intelligence tab, in the main Sumo Logic menu, select Manage Data > Logs > Threat Intelligence.
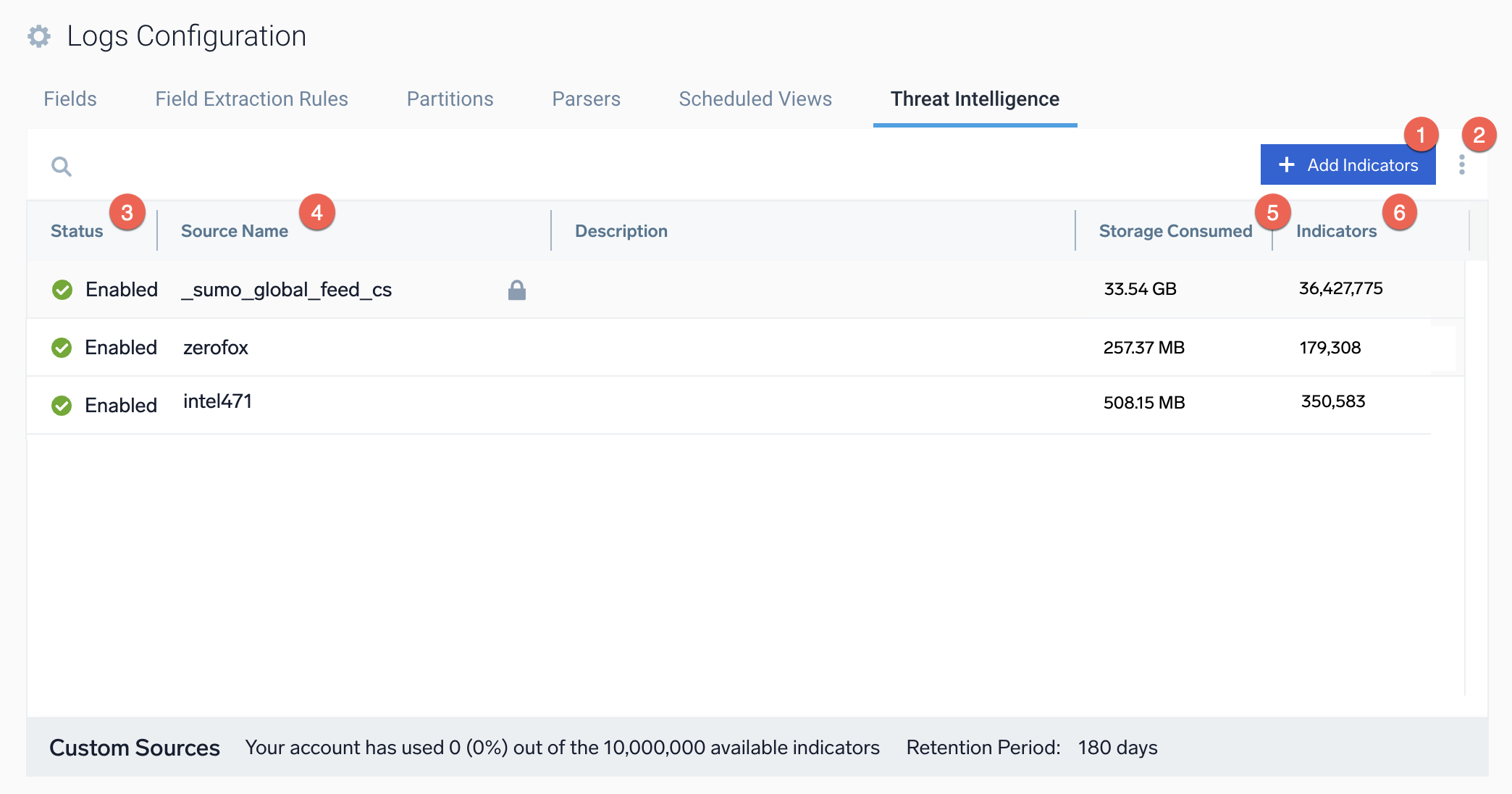
- + Add Indicators. Click to upload files that add threat intelligence indicators.
- Actions. Select to perform additional actions:
- Edit Retention Period. Enter the length of time in days to retain expired threat intelligence indicator files. The maximum number of days is 180. See Change the retention period for expired indicators.
- Status. The current status of the indicator source (Enabled or Disabled).
- Source Name. The name of the threat intelligence indicator file. The name usually indicates the supplier of the indicators.
- Storage Consumed. The amount of storage consumed by the threat intelligence indicator file.
- Indicators. The number of threat intelligence indicators included in the file.
- The
SumoLogic_ThreatInteland_sumo_global_feed_cssources are default sources and cannot be changed or deleted. - The default storage limit is 10 million total indicators (not including any indicators provided by Sumo Logic such as in the
SumoLogic_ThreatInteland_sumo_global_feed_cssources).
Add Indicators button
You can add threat intelligence indicators with the Add Indicators button in the Threat Intelligence tab. For information on the other methods, see Ingest threat intelligence indicators.
Only Cloud SIEM administrators can add threat intelligence indicators to the datastore.
- New UI. In the main Sumo Logic menu select Data Management, and then under Logs select Threat Intelligence. You can also click the Go To... menu at the top of the screen and select Threat Intelligence.
Classic UI.In the main Sumo Logic menu, select Manage Data > Logs > Threat Intelligence. - Click + Add Indicators. The dialog displays.
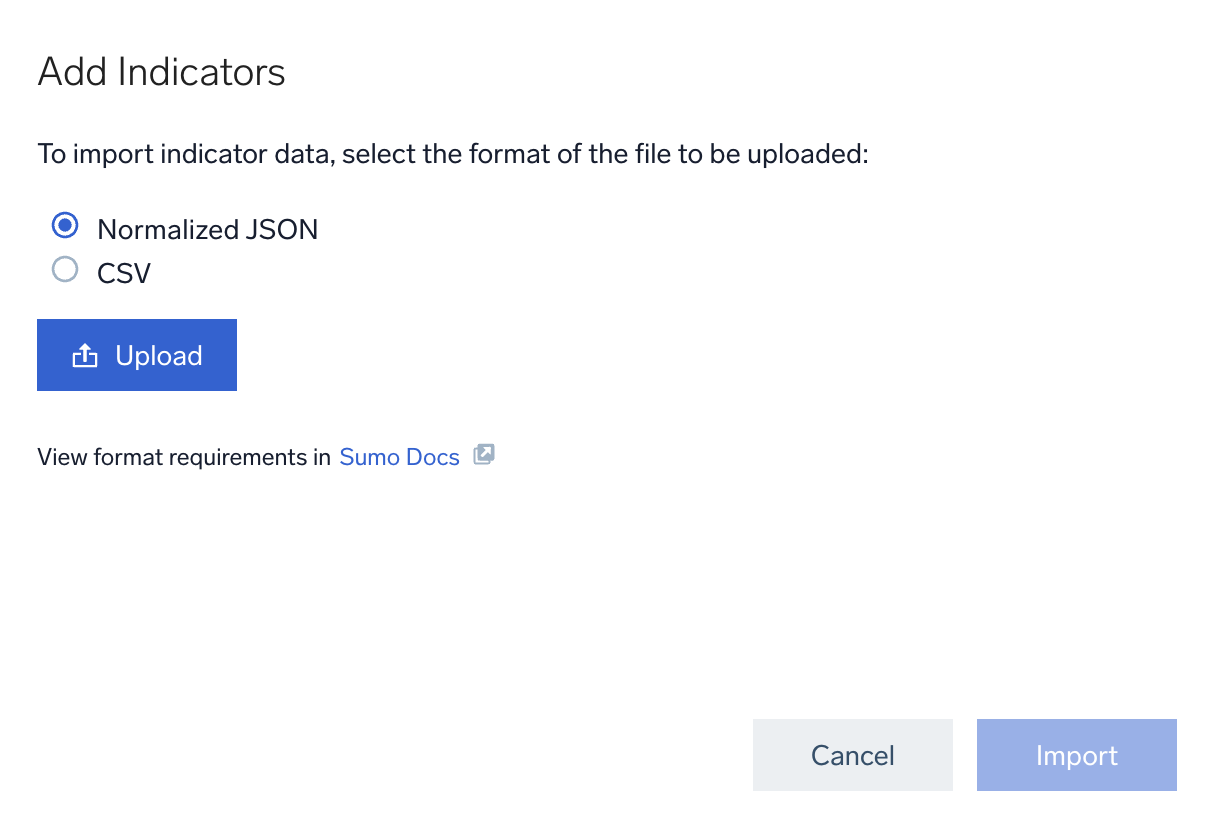
- Select the format of the file to be uploaded (see Upload formats for the format to use in the file):
- Normalized JSON. A normalized JSON file.
- CSV. A comma-separated value (CSV) file.
- Click Upload to upload the file.
- Click Import.
When you add indicators, the event is recorded in the Audit Event Index. See Audit logging for threat intelligence.
Delete threat intelligence indicators
- New UI. In the main Sumo Logic menu select Data Management, and then under Logs select Threat Intelligence. You can also click the Go To... menu at the top of the screen and select Threat Intelligence.
Classic UI. In the main Sumo Logic menu, select Manage Data > Logs > Threat Intelligence. - Select a source in the list of sources. Details of the source appear in a sidebar.
- Click the Delete Indicators button.
- Click Delete on the Delete Indicators dialog.
When you remove indicators, the event is recorded in the Audit Event Index. See Audit logging for threat intelligence.
Change the retention period for expired indicators
Indicators are deemed valid until they reach the date set by their "valid until" attribute (validUntil for normalized JSON and CSV, and valid_until for STIX). After that date, they are considered expired.
Expired indicators are retained until they reach the end of the retention period. At the end of the retention period, expired indicators are automatically deleted. Between the time they expire and are deleted, the indicators are still in the system, and you can still use them to find threats.
By default, expired indicators are retained for 180 days. To change the retention period:
- New UI. In the main Sumo Logic menu select Data Management, and then under Logs select Threat Intelligence. You can also click the Go To... menu at the top of the screen and select Threat Intelligence.
Classic UI.In the main Sumo Logic menu, select Manage Data > Logs > Threat Intelligence. - Click the three-dot button in the upper-right corner of the page.
- Click Edit Retention Period.
- Enter the length of time in days to retain expired threat intelligence indicator files. The maximum number of days is 180.
When you change the retention period, the event is recorded in the Audit Event Index. See Audit logging for threat intelligence.
You do not have to wait until indicators reach the end of their retention period in order to delete them. You can use the Threat Intelligence tab to delete indicators, as well as use the APIs in the Threat Intel Ingest Management API resource.